pic
This commit is contained in:
@ -18,7 +18,7 @@ categories: Pwn二进制漏洞
|
|||||||
- Metasploit框架-[下载](https://www.metasploit.com/)
|
- Metasploit框架-[下载](https://www.metasploit.com/)
|
||||||
- 靶机–Windows XP sp3
|
- 靶机–Windows XP sp3
|
||||||
|
|
||||||

|

|
||||||
- 函数调用与栈:调用、返回
|
- 函数调用与栈:调用、返回
|
||||||
- 寄存器与函数栈帧:ESP、EBP
|
- 寄存器与函数栈帧:ESP、EBP
|
||||||
- 函数栈帧:局部变量、栈帧状态值、函数返回地址
|
- 函数栈帧:局部变量、栈帧状态值、函数返回地址
|
||||||
@ -46,7 +46,7 @@ voidfunc(int a, int b, int c)
|
|||||||
* pop ebp
|
* pop ebp
|
||||||
* RETN【弹出返回地址,跳转】
|
* RETN【弹出返回地址,跳转】
|
||||||
3. 栈帧结构
|
3. 栈帧结构
|
||||||

|

|
||||||
|
|
||||||
# 0x01 简单栈溢出
|
# 0x01 简单栈溢出
|
||||||
|
|
||||||
@ -63,7 +63,7 @@ voidfunc(int a, int b, int c)
|
|||||||
> `quit`
|
> `quit`
|
||||||
|
|
||||||
## 漏洞点
|
## 漏洞点
|
||||||

|

|
||||||
|
|
||||||
**产生崩溃**
|
**产生崩溃**
|
||||||
将输出的1024个A发送给靶机程序
|
将输出的1024个A发送给靶机程序
|
||||||
@ -71,44 +71,44 @@ voidfunc(int a, int b, int c)
|
|||||||
python -c "print('A' * 1024)"
|
python -c "print('A' * 1024)"
|
||||||
telnet 192.168.64.138 4242
|
telnet 192.168.64.138 4242
|
||||||
```
|
```
|
||||||

|

|
||||||
|
|
||||||
## 关闭防御措施
|
## 关闭防御措施
|
||||||
使用**PESecurity**检查可执行文件本身的防御措施开启情况
|
使用**PESecurity**检查可执行文件本身的防御措施开启情况
|
||||||
注意设置:Set-ExecutionPolicyUnrestricted
|
注意设置:Set-ExecutionPolicyUnrestricted
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
**ASLR和DEP**
|
**ASLR和DEP**
|
||||||
ASLR在xp下不用考虑,DEP可通过修改boot.ini中的nonexecute来完成(AlwaysOff、OptOut)
|
ASLR在xp下不用考虑,DEP可通过修改boot.ini中的nonexecute来完成(AlwaysOff、OptOut)
|
||||||

|

|
||||||
|
|
||||||
## 整体的攻击流程
|
## 整体的攻击流程
|
||||||
1. 任意非00的指令覆盖buffer和EBP
|
1. 任意非00的指令覆盖buffer和EBP
|
||||||
2. 从程序已经加载的dll中获取他们的jmp esp指令地址。
|
2. 从程序已经加载的dll中获取他们的jmp esp指令地址。
|
||||||
3. 使用jmp esp的指令地址覆盖ReturnAddress
|
3. 使用jmp esp的指令地址覆盖ReturnAddress
|
||||||
4. 从下一行开始填充Shellcode
|
4. 从下一行开始填充Shellcode
|
||||||

|

|
||||||
|
|
||||||
## 确定溢出点的位置
|
## 确定溢出点的位置
|
||||||
1. 生成字符序列 **pattern_create.rb**
|
1. 生成字符序列 **pattern_create.rb**
|
||||||

|

|
||||||
|
|
||||||
2. 发送给目标程序
|
2. 发送给目标程序
|
||||||

|

|
||||||
|
|
||||||
3. 计算偏移量 **pattern_offset.rb**
|
3. 计算偏移量 **pattern_offset.rb**
|
||||||

|

|
||||||
|
|
||||||
4. 确定payload结构
|
4. 确定payload结构
|
||||||

|

|
||||||
|
|
||||||
## 寻找jmp esp跳板
|
## 寻找jmp esp跳板
|
||||||
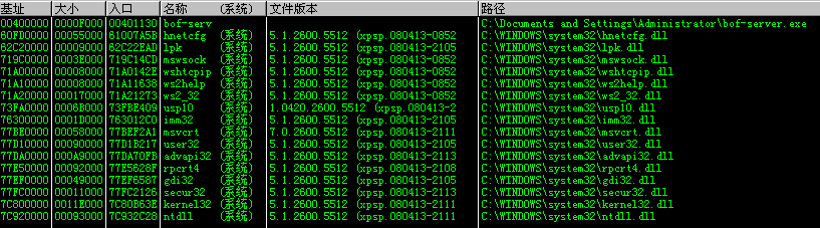
1. OD附加进程看一下服务器加载了哪些模块
|
1. OD附加进程看一下服务器加载了哪些模块
|
||||||

|
|
||||||
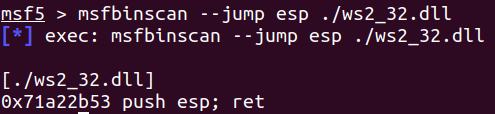
2. 查找JMP ESP指令的地址
|
2. 查找JMP ESP指令的地址
|
||||||
在这里选择了ws2_32.dll作为对象,通过Metasploit的msfbinscan进行搜索
|
在这里选择了ws2_32.dll作为对象,通过Metasploit的msfbinscan进行搜索
|
||||||

|
|
||||||
|
|
||||||
## 自动化攻击
|
## 自动化攻击
|
||||||
```ruby=
|
```ruby=
|
||||||
@ -226,7 +226,7 @@ vim -bz.txt
|
|||||||
- 将Easy File Sharing Web Server 7.2加载到ImmunityDebugger中,并处于运行状态。
|
- 将Easy File Sharing Web Server 7.2加载到ImmunityDebugger中,并处于运行状态。
|
||||||
- 发送溢出字符序列
|
- 发送溢出字符序列
|
||||||
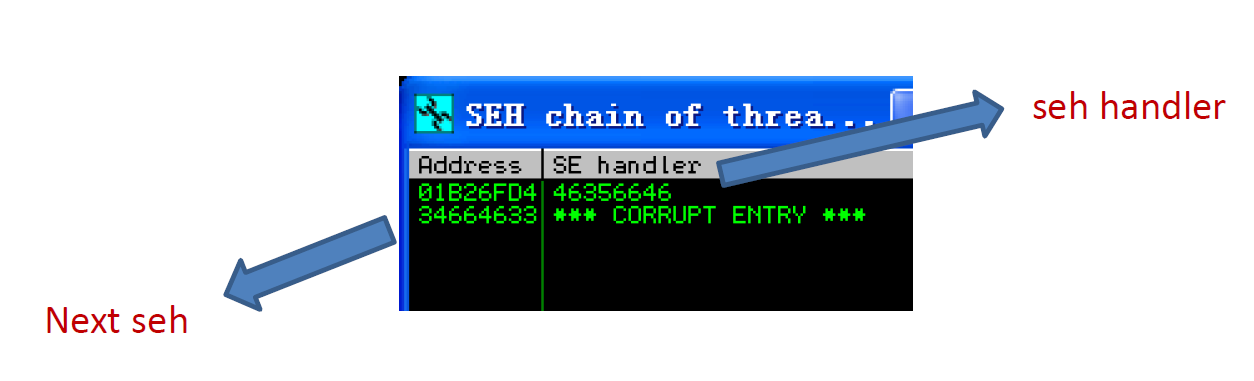
- 查看Easy File Sharing Web Server 7.2溢出地址
|
- 查看Easy File Sharing Web Server 7.2溢出地址
|
||||||

|
|
||||||
|
|
||||||
3. 计算偏移量
|
3. 计算偏移量
|
||||||
计算catch块偏移量&计算下一条SEH记录偏移量
|
计算catch块偏移量&计算下一条SEH记录偏移量
|
||||||
@ -325,7 +325,7 @@ Server username: WHU-3E3EECEBFD1\Administrator
|
|||||||
> **漏洞点** 
|
> **漏洞点** 
|
||||||
|
|
||||||
## 设置DEP保护
|
## 设置DEP保护
|
||||||

|

|
||||||
*构建ROP链来调用VirtualProtect()关闭DEP并执行Shellcode*
|
*构建ROP链来调用VirtualProtect()关闭DEP并执行Shellcode*
|
||||||
|
|
||||||
## 计算偏移量
|
## 计算偏移量
|
||||||
|
|||||||
Reference in New Issue
Block a user